Hysolate Platform
Photo Gallery
 |
 |
Hysolate Platform

Additional Info
| Company | Hysolate |
| Website | http://www.hysolate.com |
| Company size (employees) | 10 to 49 |
| Type of solution | Software |
Overview
Cyberattackers target privileged users in order to access privileged accounts. A Cybersecurity Insider study found more than 85 percent of cybersecurity professionals believe isolating privileged environments is critical to protecting corporate crown jewels.
However, traditional approaches to privileged access result in high IT labor and CapEx costs, lost productivity, and frustrated end-users.
Even if they segment networks and protect privileged credentials with Privileged Access Management, attackers who compromise privileged users’ workstations can immediately interact in the user’s name to access sensitive assets, leak data or do harm. To combat this, many companies give each privileged user two separate physical devices: one for day-to-day corporate work and Internet access, and another — often called a Privileged Access Workstation (PAW) — that’s fully locked down and dedicated to sensitive tasks and information.
This physical air gap strategy isn’t sustainable. Each privileged user loses about five hours of productivity/week due to shifting back-and-forth between workstations. When travelling, they lug around two devices. The IT team manages twice the inventory, and then there’s the cost of maintaining extra physical devices.
The Hysolate Platform enables a radically different, much more effective approach to PAW. For the first time, each user has multiple, fully isolated environments on a single physical device, separated via a virtual air gap.
Hysolate is the only solution that uses virtualization to seamlessly split a single physical workstation into multiple, completely separate local virtual machines (VMs), each with its own segregated operating system (OS). It does this in a way that is seamless to the end-user. Everything the user interacts with – including all applications and OSes – runs in the appropriate VM. Cyberattackers cannot access privileged information or even see that it exists.
In contrast to traditional PAW approaches, Hysolate’s results in lower IT labor and CapEx costs, gained productivity, and happy end-users.
How we are different
● Hysolate Rearchitected Endpoints for Privileged Workstation Security
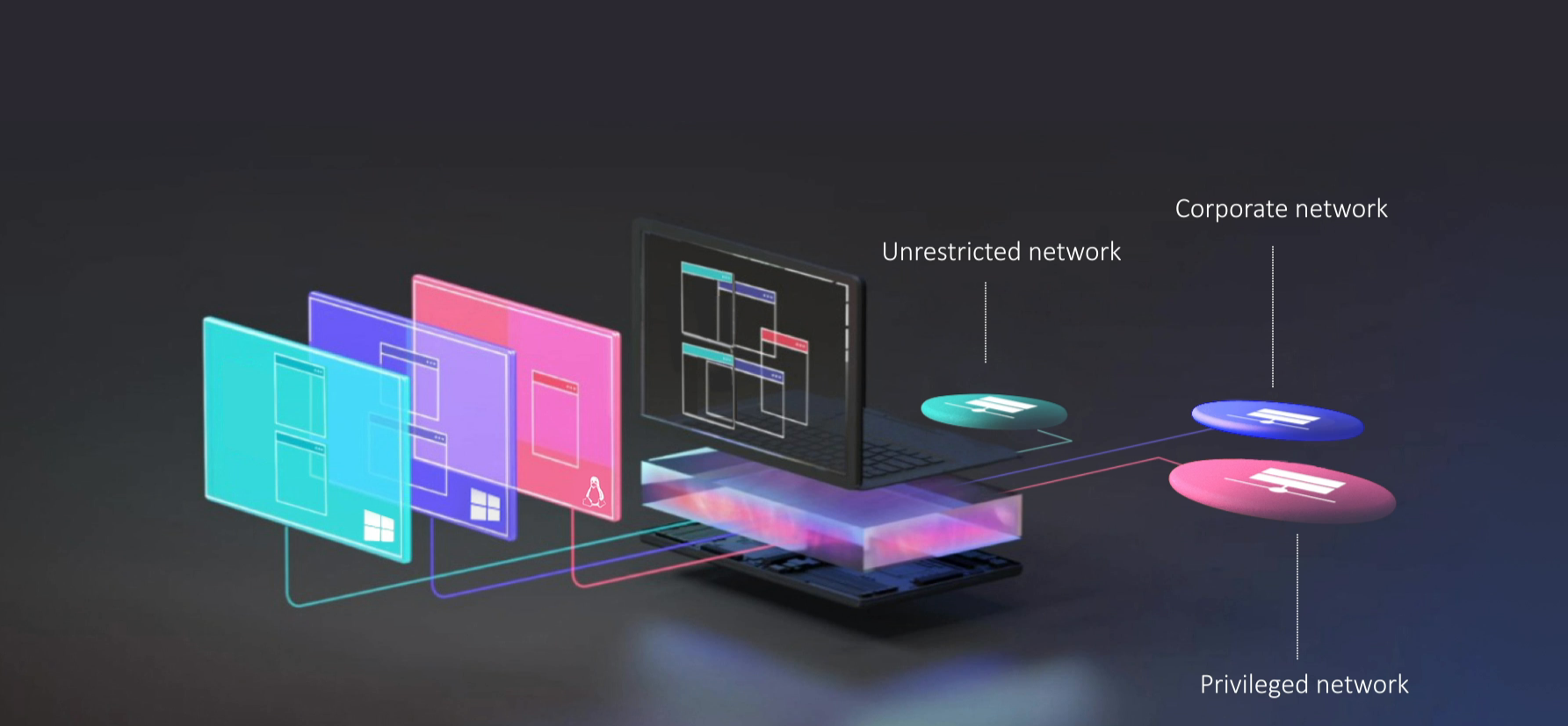
With Hysolate, the physical endpoint is controlled by a hardened bare-metal hypervisor. The hypervisor manages 2-3 isolated VMs running locally on the workstation, one per user persona/security zone. A typical set of virtual air gapped VMs that run side-by-side includes:
-Fully locked-down privileged VM for accessing sensitive corporate data and systems, e.g., IT systems, payment/transaction systems, sensitive customer data, CRM systems.
-Unlocked VM for unrestricted access to non-corporate resources, e.g., browsing the full web, installing any application, using external devices.
-Semi-locked-down corporate VM for accessing standard corporate applications, e.g., office documents, corporate email, internal services.
● Hysolate Blocks Cyberattackers from Privileged Information
Hysolate ensures hackers cannot move laterally in the network to access privileged information. Malware on internet-exposed VMs cannot reach or see sensitive resources, which are only accessible via the privileged VM. Malware can only access the VM that it’s contained within -- which can be wiped clean by Hysolate.
Each VM’s network access is limited according to the security zone it belongs to. The internet VM can only access the wild internet; the corporate VM can only access non-privileged corporate network, the privileged VM can only access privileged resources on the network.
● Hysolate Keeps Privileged Users Productive, Costs Down
End-users access, install and work with privileged and non-privileged information using a one physical workstation, without signing into the separate environments. Their endpoint looks like a single unified Windows desktop. Applications and websites launch automatically in the correct VM due to Hysolate’s unique application redirection.
There’s no swiveling or lugging multiple laptops. Privileged users can access the resources they need, without endangering/compromising corporate assets.
IT saves management and troubleshooting time, and doesn’t have the costs associated with multiple laptops per user.



