i-Sprint’s AccessMatrix™ Universal Authentication Server (UAS)
Photo Gallery
 |
 |
i-Sprint’s AccessMatrix™ Universal Authentication Server (UAS)


Additional Info
| Company | i-Sprint Innovations Pte Ltd |
| Website | https://www.i-sprint.com/ |
| Company size (employees) | 100 to 499 |
| Headquarters Region | Asia |
| Type of solution | Software |
Overview
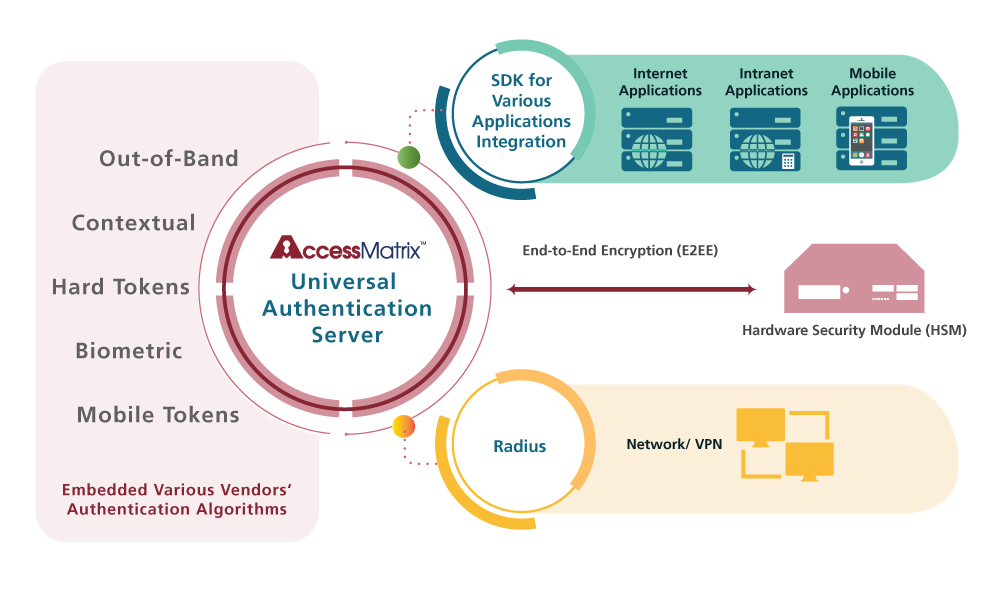
AccessMatrix™ Universal Authentication Server (UAS) is an inclusive and versatile authentication server solution that enables businesses to consolidate its different authentication systems on to a single unified platform. It offers the freedom for organizations to deploy various authentication methods from different vendors under one platform and manage it as a holistic security approach.
UAS future-proof authentication infrastructure supports multiple authentication methods (such as passwords, hardware token, software token, OTP, biometrics) for strong authentication and authorization requirements. This means businesses are not restricted by or locked in to a specific hardware or software authentication solution. The use of Pluggable Authentication Module (PAM) approach also allows businesses to have the ease of adding new authentication methods when available on top of their existing ones.
Based on the proven AccessMatrix™ Integrated Security Architecture, UAS provides security Administration, Authentication, Authorization, and Audit services (4As) for business applications. In addition to authentication, it provides:
• End-to-End Life Cycle Management for OTP Tokens
• Security services APIs for application integration and shield the complexity of token integration
• RADIUS ready server to integrate with network devices
• Administration module for administration delegation and user management
• Audit and reporting module
• Hardware Security Module (HSM) interface to leading brands of HSM devices
• PIN mailer interface for mail merge and secure printing
• Enforcing password policy – password history, password aging, password quality check, etc
How we are different
1) i-Sprint’s latest UAS solution offers businesses the flexibility to deploy different authentication methods by multiple vendors on a single platform, and yet it is able to manage it as one holistic security approach.
2) The use of the Pluggable Authentication Module (PAM) method allows businesses to easily add new authentication options, simplify integration and deployment efforts and it provides a highly scalable, open and reliable platform.
3) UAS provides a Complete Token Life Cycle Management & Administration that include issuance, delivery, out of sync, lost token, temporary access, replacement over time and other supporting functions such as ePIN mailer integration and reporting module.



