Illusive Networks Insider Threat Detection and Response
Photo Gallery
 |
 |
Illusive Networks Insider Threat Detection and Response

Additional Info
| Company | Illusive Networks |
| Website | http://www.illusivenetworks.com |
| Company size (employees) | 100 to 499 |
| Type of solution | Cloud/SaaS |
Overview
Founded by former nation-state attackers to stop other attackers, the mission of Illusive Networks is to deliver deception-based technology to detect and stop human-driven cyberattacks early in the breach process before they can do damage.
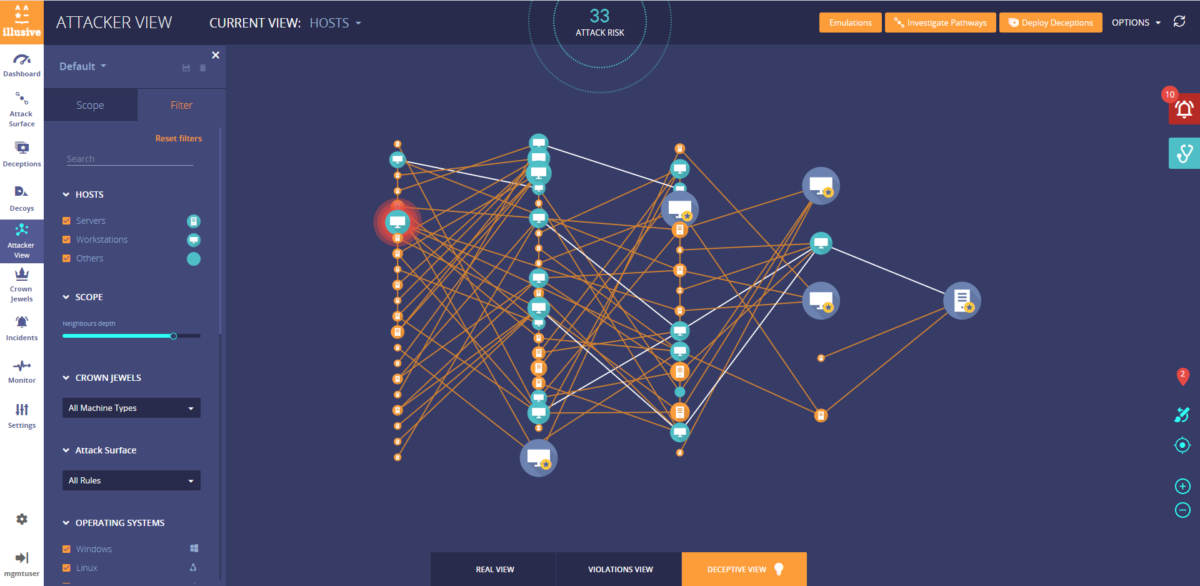
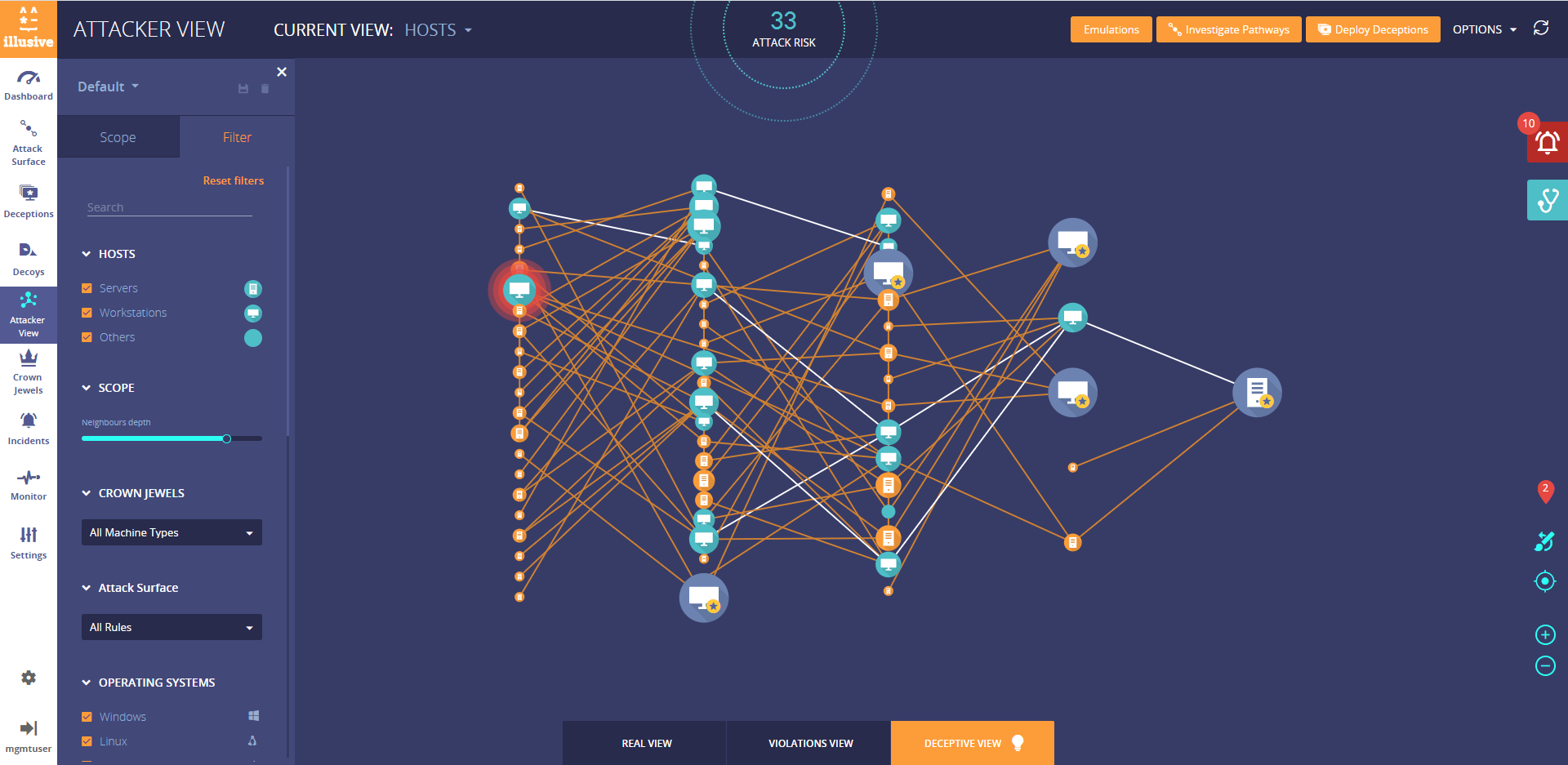
Insiders are potentially more dangerous than the outside attacker because they already have a degree of trusted access and direct insight into an organization’s crown jewels. But in most cases, the nefarious insider must first snoop around file systems and acquire credentials to connect to systems they aren’t authorized to access – just like an outside attacker. This lateral movement prevention is key to stopping any type of attacker.
Illusive’s inescapable deception technology is designed to directly address the “living off the land” tactics of today’s threat actors, who shroud their reconnaissance, lateral movement and activity in legitimate connectivity and credentials to evade detection. By detecting underlying attacker behavior through deceptive data meant to fool attackers into engagement, Illusive’s technology is not reliant on known threat signatures, nor does it have the potential to fall behind as new malware and attack tools evolve.
Instead of alerting on policy violations or relying on complex data analytics, a deception approach provides a very simple method to identify malicious behavior by detecting the actions attackers must use to find and move toward valuable assets. Once a bad actor engages with a deceptive file, they’ll trigger a notification filled with detail rich source forensics. Armed with this incontrovertible evidence, the organization will be well armed to take appropriate action.
How we are different
• Illusive focuses first on removing any unnecessary pathways to critical assets. Most networks are not really segmented as intended; rogue or “shadow” connections between systems remain, often as remnants of IT projects or service tickets. By focusing on this task first, Illusive is limiting the fuel that attackers need to live off the land, mask their malicious activity behind legitimate connections and credentials, and launch attacks undetected.
• Since deception does not rely on established access patterns or user behavior, rapid environmental change, such as the massive migration to remote work, has no effect on detection efficacy. Detection is based on the simplest of algorithms – either an attacker interacted with a deception or they did not. Massively distributed, highly authentic deceptions force nefarious actors to unknowingly interact to progress their attack. When an Illusive notification fires, it’s not white noise – this incident requires immediate investigation. The deterministic detection provided by Illusive is in contrast to most threat detection platforms that rely on probabilistic risk thresholds that require further investigation to confirm whether an attack is truly in progress.
• Unlike SIEM and security logs, which can be used to piece together a picture of an incident once identified, Illusive flags the malicious activity as it happens and begins recording everything that is taking place on that system. The full forensic picture is then delivered to security teams for remediation and further action, saving countless hours of investigation time.



