Nucleus Cyber NC Protect
Photo Gallery
 |
|
Nucleus Cyber NC Protect


Additional Info
| Company | Nucleus Cyber |
| Website | https://nucleuscyber.com/ |
| Company size (employees) | 10 to 49 |
Overview
NC Protect is content and context aware to automatically find, classify and secure unstructured data on-premises, in the cloud and in hybrid environments. It protects against breaches, sensitive data misuse and unauthorized file access enabling enterprises to prevent insider threats and secure enterprise collaboration tools. NC Protect dynamically adjusts file security based on real-time comparison of user context and file content to make sure users view, use and share files according to organizational and regulatory policies.
With NC Protect enforce compliance and data security policies for privacy and confidentiality, intellectual property and trade secret protection, data loss prevention, enterprise social communications, PII and PCI compliance, HIPAA requirements, and other governance factors. It ensures data compliance and security by continuously monitoring and auditing data and documents against these policies to protect against data breaches, unauthorized access and misuse.
NC Protect augments access controls using the unique identity a file builds over time from the moment it is first saved, with its content, name, authorship and date stamps. Through its lifecycle it gains additional transient context such as the file location or information repository, and classification levels. Real-time access controls reflect the user’s current context, blending traditional user permissions with granular business information such as security level or project team. Additionally, NC Protect leverages transient context such as location, IP address, device, browser or time of day.
The platform is fully integrated with Microsoft Office 365, SharePoint, Teams, Yammer, Dropbox, and file shares. It works natively with Microsoft products and enhances security to restrict the use of Microsoft functionality, including elements of the SharePoint user interface, methods for viewing files, and encryption or restriction of attachments sent through Exchange Email. It requires no additional client-side application, reducing IT overhead and the risks involved in implementing new cloud services or BYOD policies.
How we are different
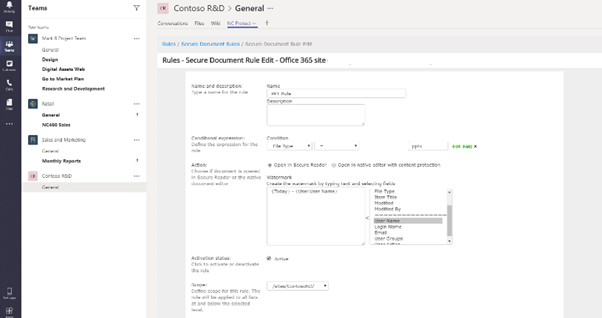
• NC Protect offers a centralized and cost-effective intelligent data-centric security solution for enterprise collaboration in Office 365 apps, Dropbox and file shares to ensure compliance with regulatory and corporate policies and protect against insider breaches to mitigate risk. IT administrators define access rules and usage rights to efficiently and dynamically control access and user actions without the need to create separate sites and security groups.
• NC Protect takes an organization’s data security policies and enforces them for each and every user and device and is completely transparent to the end user for a seamless security and user experience.
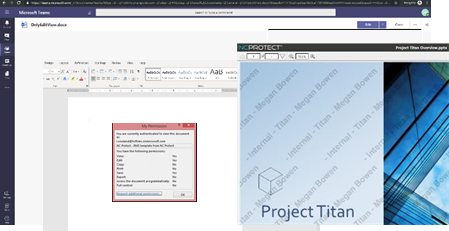
• With unique features such as dynamic watermarks and in-app rule creation within Microsoft Teams, NC Protect provides Teams Owners with unparalleled capabilities for defining and applying information protection to their file and chat data.



