Picus Security
Photo Gallery
 |
 |
Picus Security

Additional Info
| Website | http://www.picussecurity.com |
| Company size (employees) | 100 to 499 |
| Headquarters Region | North America |
Overview
At Picus Security, we prioritize making it easy for organizations to consistently validate and enhance their resilience against cyber attacks. By leveraging our easy to manage platform, security teams can better quantify risk, maximize security effectiveness, and use automation to amplify impact.
Trusted by industry leaders such as Mastercard, ING and Palo Alto, the Picus Complete Security Validation Platform simulates real-world threats and uses cutting-edge GenAI to discover at-risk assets, measure the effectiveness of security controls, manage high-risk attack paths, and optimize threat prevention and detection capabilities.
How we are different
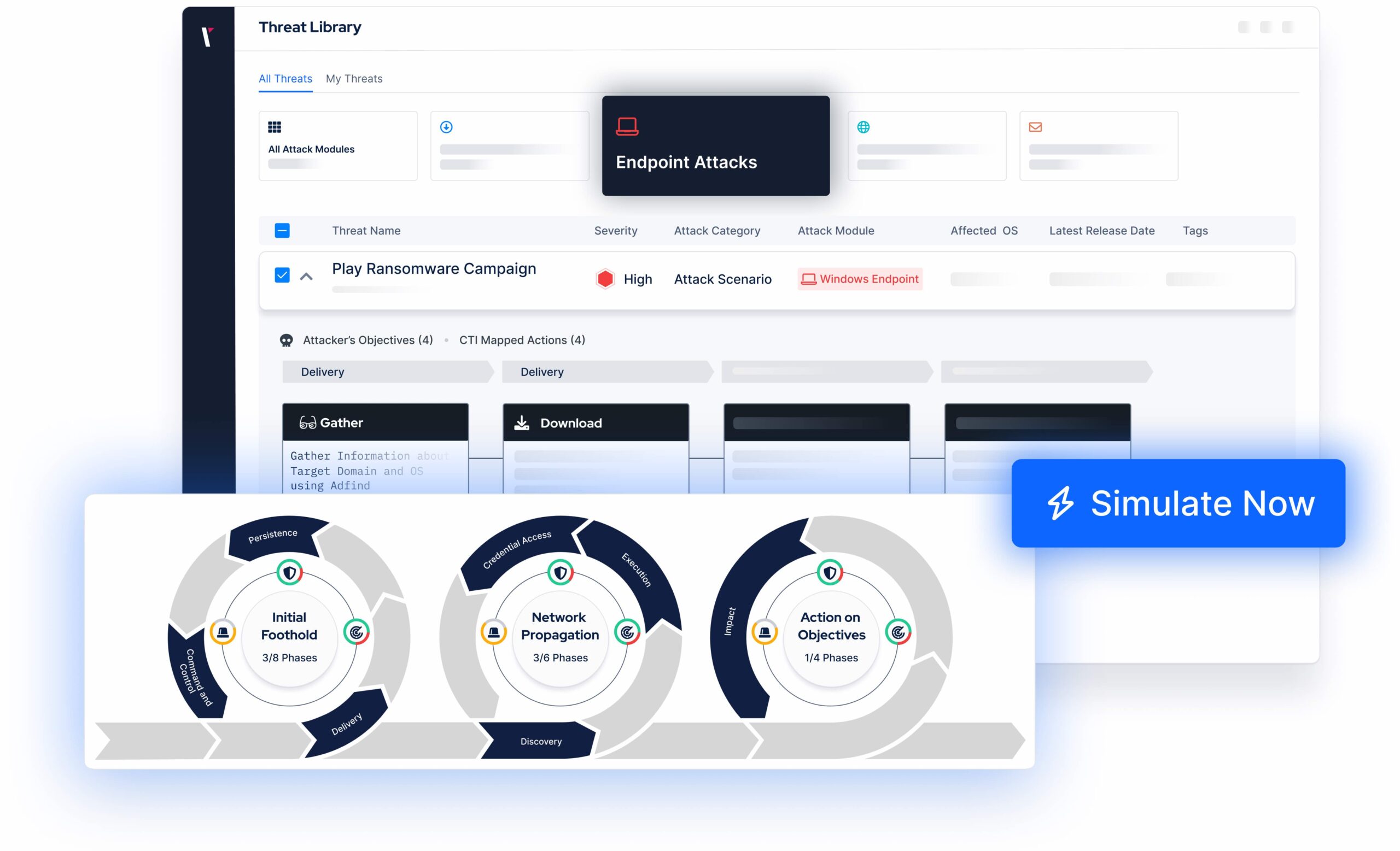
- The Picus Platform is the most extensive security validation platform available today. Key use cases the platform addresses include Breach and Attack Simulation, Continuous Threat Exposure Management, SOC Optimization, Attack Path Management, Penetration Testing Automation, Attack Surface Management, Cloud Security Posture Management, and Ransomware Readiness.
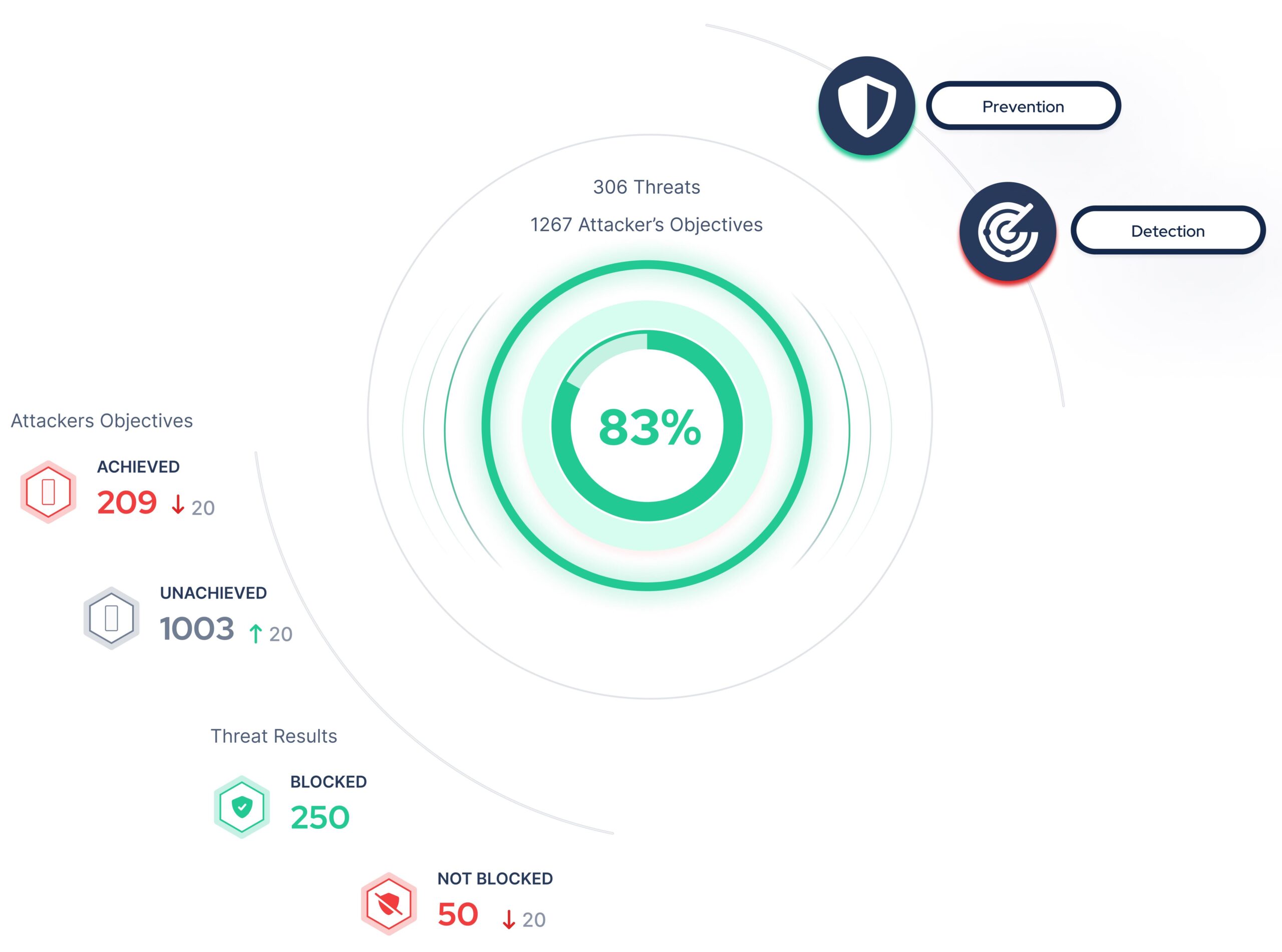
- Picus believes that security validation should be quick and easy for every organization, even those without extensive security resources. It’s why the Picus Security Validation Platform is fast to deploy, easy to manage and does not require specialist offensive security expertise to use. On average, organizations that deploy the Picus platform see a 2x increase in their ability to block threats in just three months.
- Over the last 12 months, Picus has continued to enhance the capabilities of its platform to help organizations broaden the scope of security validation and prioritize risks more intelligently. Recent enhancements include the release of Attack Surface Validation (to discover internal and external assets), Picus Cyber Threat Intelligence (to guide threat profiling based on an organization’s context), and the integration of GenAI (to deliver easily accessible insights to guide risk prioritization and mitigation). When it comes to optimizing security controls, for example, no other vendor supplies such an extensive range of vendor-specific content, including prevention signatures for firewalls and detection rules for SIEM and EDR solutions.
-
Vote for this Nomination
(click the thumbs-up icon to cast your vote)

 (13 votes)
(13 votes)You need to be a registered member to vote for this nomination. Please register here.


