Proofpoint Cloud App Security Broker, Web Security, Browser Isolation and Zero Trust Network Access (ZTNA)
Photo Gallery
 |
 |
Proofpoint Cloud App Security Broker, Web Security, Browser Isolation and Zero Trust Network Access (ZTNA)

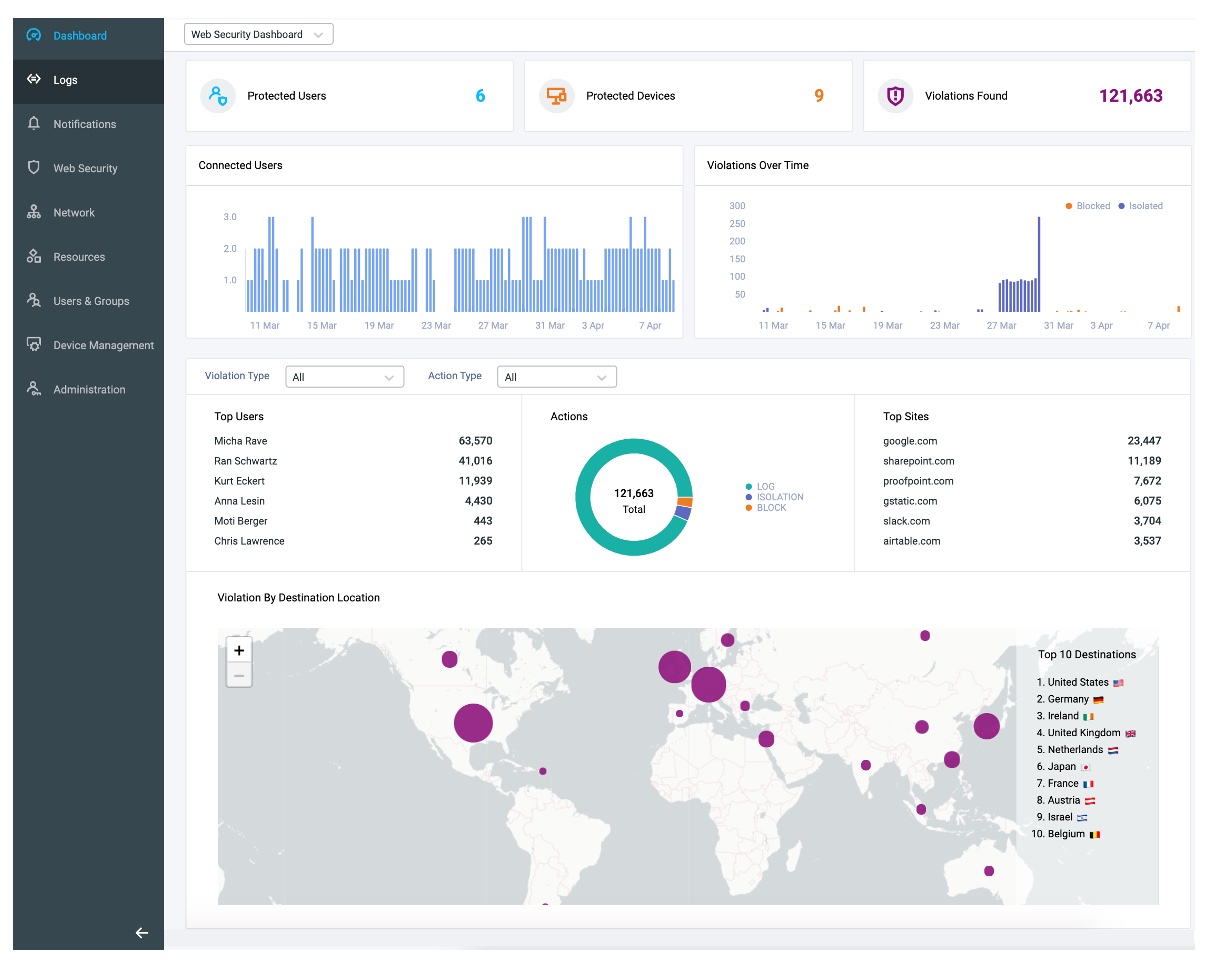
Additional Info
| Company | Proofpoint |
| Website | https://www.proofpoint.com/us |
| Company size (employees) | 1,000 to 4,999 |
| Type of solution | Cloud/SaaS |
Overview
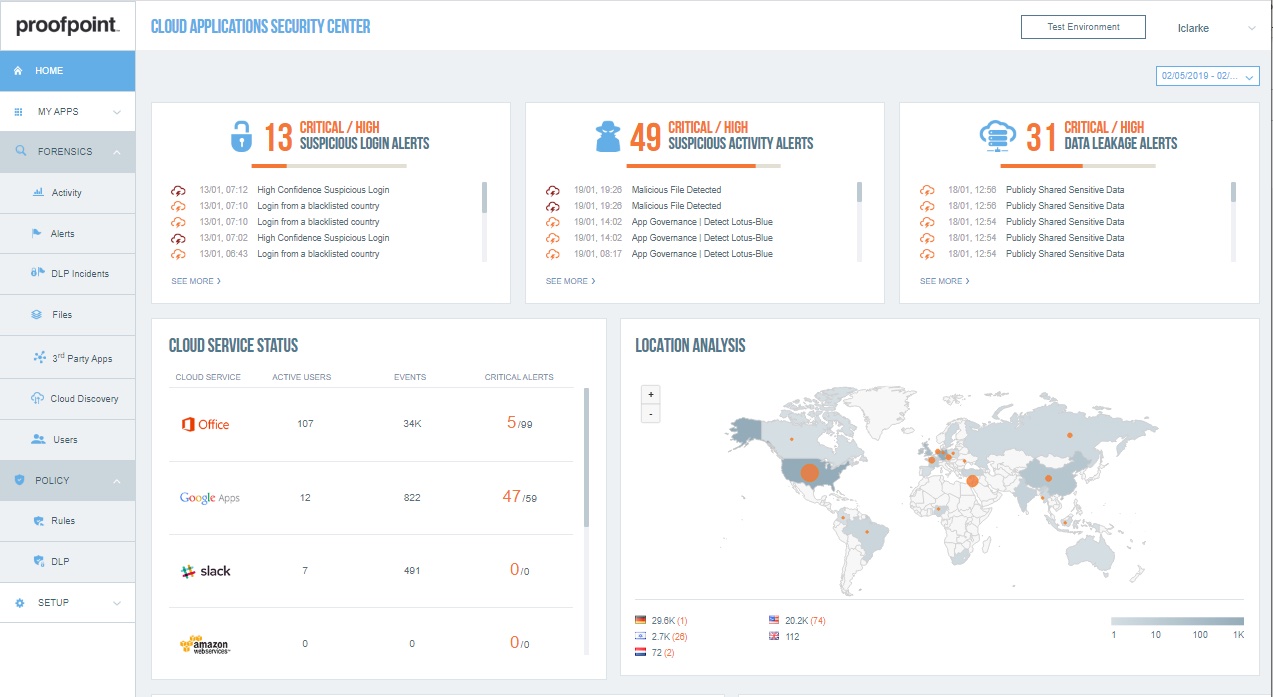
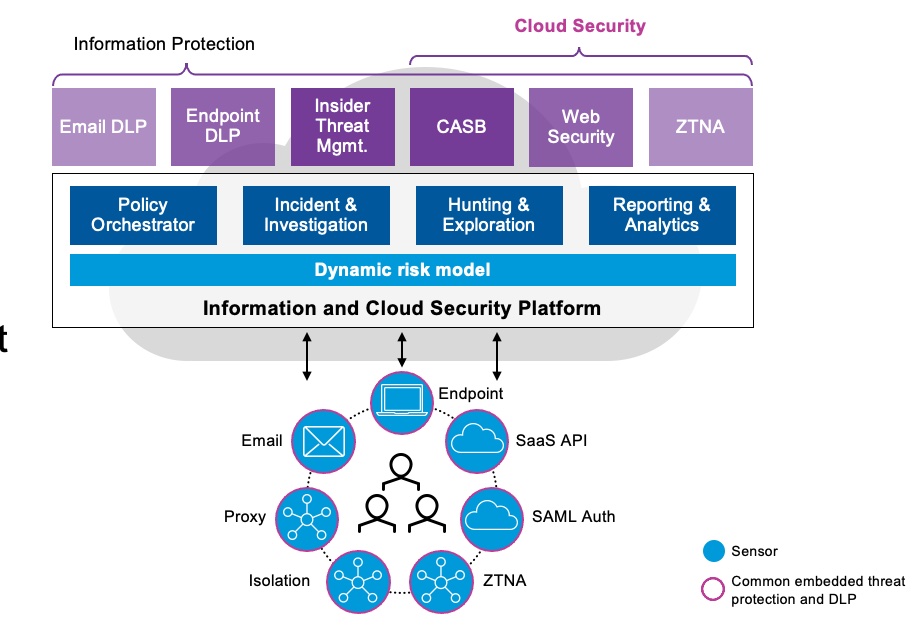
Increasing threat activity, difficulty over monitoring a remote workforce and accelerating migration of data to the cloud means you have to redraw your security perimeter using a people-centric approach. Proofpoint Cloud App Security Broker (Proofpoint CASB), Web Security, Isolation across Email, Web and SaaS apps and Zero Trust Network Access (ZTNA) provide the visibility and people-centric security controls to help you identify risk, control access and protect sensitive data in the cloud. Proofpoint’s hybrid cloud security solutions protect users as they work across Microsoft 365, Google Workspace, Salesforce, Box, Slack, AWS, Azure and hundreds of other IT tolerated and approved cloud applications, be it within the browser or inside the native client.
Our hybrid cloud security solution combines:
● Compromised cloud account detection and automated response
● Protection against malicious files
● Data security including DLP
● Cloud and third-party apps governance including third-party OAuth applications
● IaaS protection, including Cloud Security Posture Management (CSPM) in AWS, Azure and Google Cloud
● Adaptive access controls for risky users and unmanaged devices, including real-time device-based controls for file transfers using Proofpoint SaaS Isolation
● In-line and real-time malware and data leakage prevention on managed devices with web apps through Web Security and IT-tolerated apps with CASB
● Secure remote access to resources in the datacenter and the cloud using Proofpoint ZTNA
● Adaptive web controls to enable user access to websites, personal email and corporate email without exposing your organization to malware and data loss through Web Security and Isolation
With Proofpoint, you can deploy consistent DLP policies across cloud, email and endpoint. You can also centralize alert management across these channels on a single console. Our powerful analytics and adaptive controls help companies grant the right levels of access to users and third-party apps based on the risk factors that matter most.
How we are different
● Proofpoint hybrid cloud security differentiates from competitors with people-centric and high-efficacy security analytics that excel at protecting users from threats, such as account compromise, malicious files, malicious apps, abuse of third-party OAuth app access, abuse of IaaS resources and initial access and preparation of ransomware attacks. Competitors fall short in the following areas: shallow depth in detecting account compromise, inability to correlate compromise with post-compromise activity that dramatically slows down security response and incomplete account takeover remediation capabilities across Microsoft, Google and Okta federated applications
● Data loss originates with people. They can be negligent, compromised, or malicious. Understanding user intent enables you to apply the appropriate DLP response to mitigate risk. Proofpoint is the only vendor that brings together the telemetry of content, user-behavior and threats across the most critical DLP channels – cloud (SaaS and IaaS storage), email, endpoint and web. Competitors fall short in either their inability to bring together the DLP channels into one console for triage and response or cant correlate threat and user behavior to the data movement.
● With Proofpoint CASB, you can govern SaaS, web and private apps as well as IaaS services in a centralized management console. We prioritise context into the apps with the most app vulnerabilities, the most attacked or abused and contain the most sensitive data or accessed by the privileged users. This includes first-party cloud apps (such as Microsoft OneDrive and Salesforce) as well as third-party (such as those created within Google Workspace, Microsoft appStore or federated through OAuth tokens). Competitors fall short by either missing the context of which apps are most abused or attacked in the real-world or lack the depth of detection capabilities in third-party apps such as OAuth authenticated apps.



