Proofpoint Threat Protection Platform
Photo Gallery
 |
 |
Proofpoint Threat Protection Platform

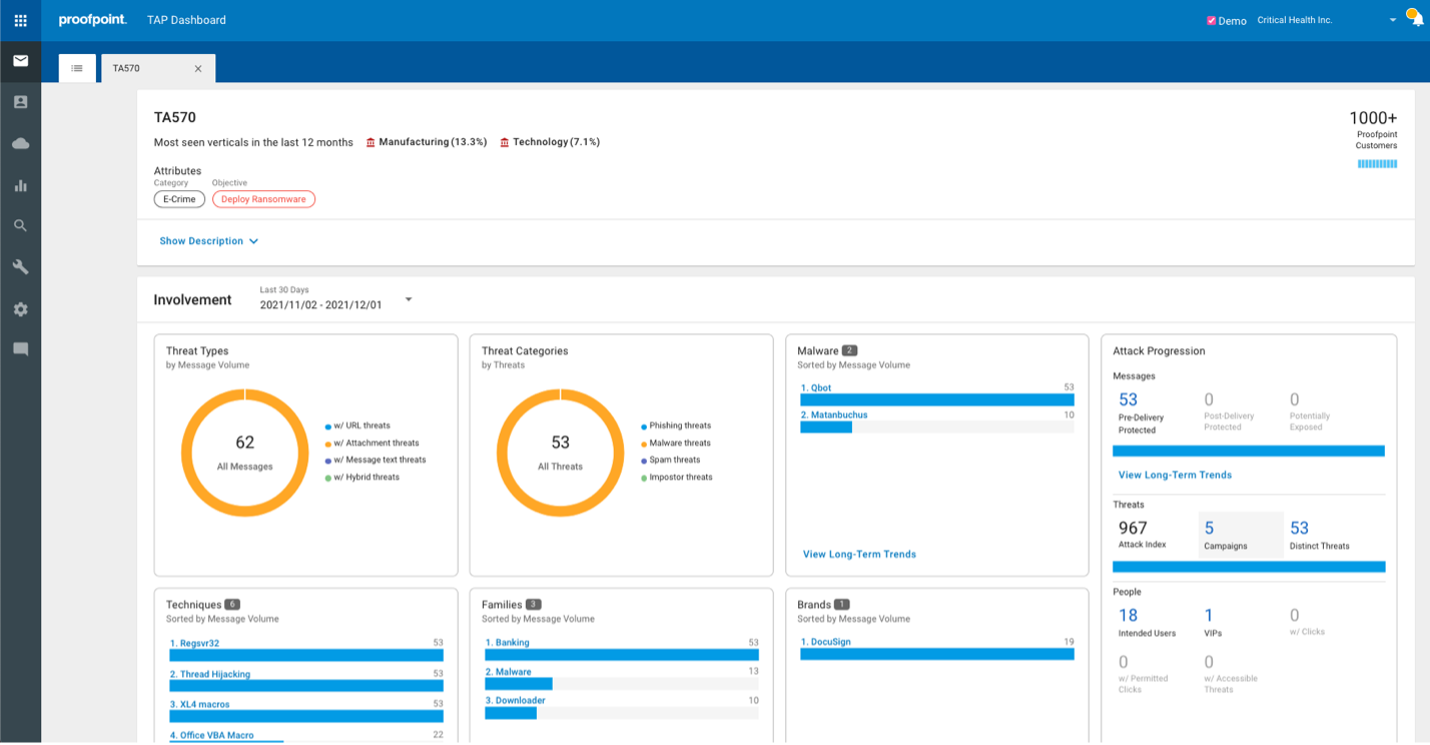
Additional Info
| Company | Proofpoint |
| Website | https://www.proofpoint.com/us |
| Company size (employees) | 1,000 to 4,999 |
| Type of solution | Cloud/SaaS |
Overview
The Proofpoint Nexus Threat Protection Platform is a people-centric solution that protects your people from the threats that target them. By integrating multiple controls across email, cloud, users and suppliers, it provides a comprehensive way to defend against phishing, BEC email fraud, malware and ransomware. This integrated platform provides unparalleled visibility into your attack surface, more effective protection against modern threats, and positive operational outcomes.
To effectively mitigate risk of email attacks, Proofpoint enables organizations to apply numerous risk-based adaptive controls, including email isolation, predictive sandboxing, and security awareness training to risky users. It dynamically isolates URL clicks based on the risk profile of the recipient and provides real-time anti-phishing scan. It preemptively sandboxes file sharing URLs before users click rather than relying solely on reputation, successfully addressing collaboration platform phishing where attackers host and deliver malicious payloads via legitimate filesharing sites. It also allows security professionals to safely assess how users would engage with impostors by simulating real-world phishing attacks and to auto-enroll those who require additional training.
With automated threat response capabilities, Proofpoint enables organizations to quickly remove phishing emails containing URLs poisoned post-delivery, even if they’re forwarded or received by others. It also streamlines abuse mailbox, enabling end-users to report suspicious emails with one click via email warning tag. User reported messages are automatically analyzed and quarantined if found to be malicious, significantly reducing manual work and IT overhead.
How we are different
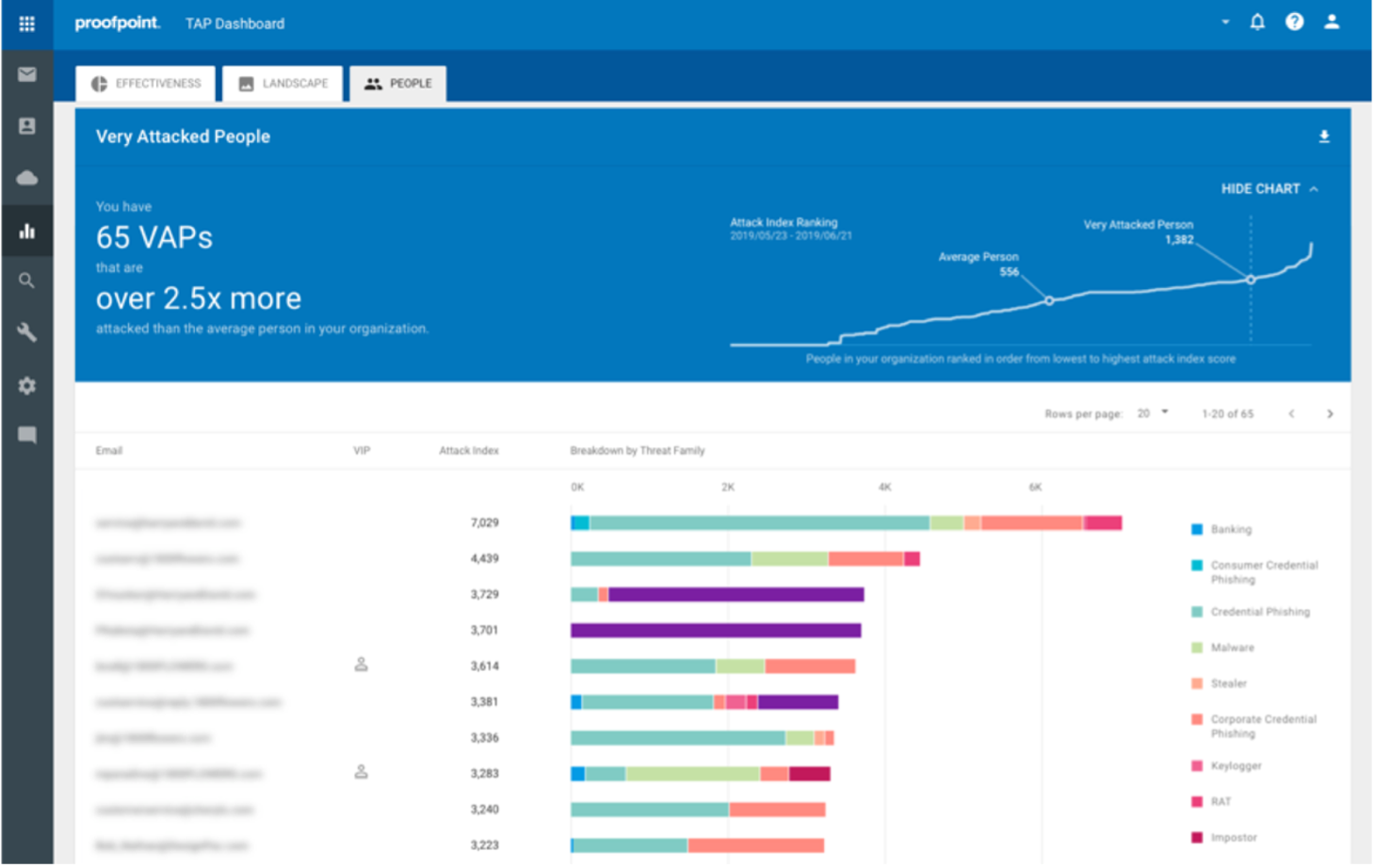
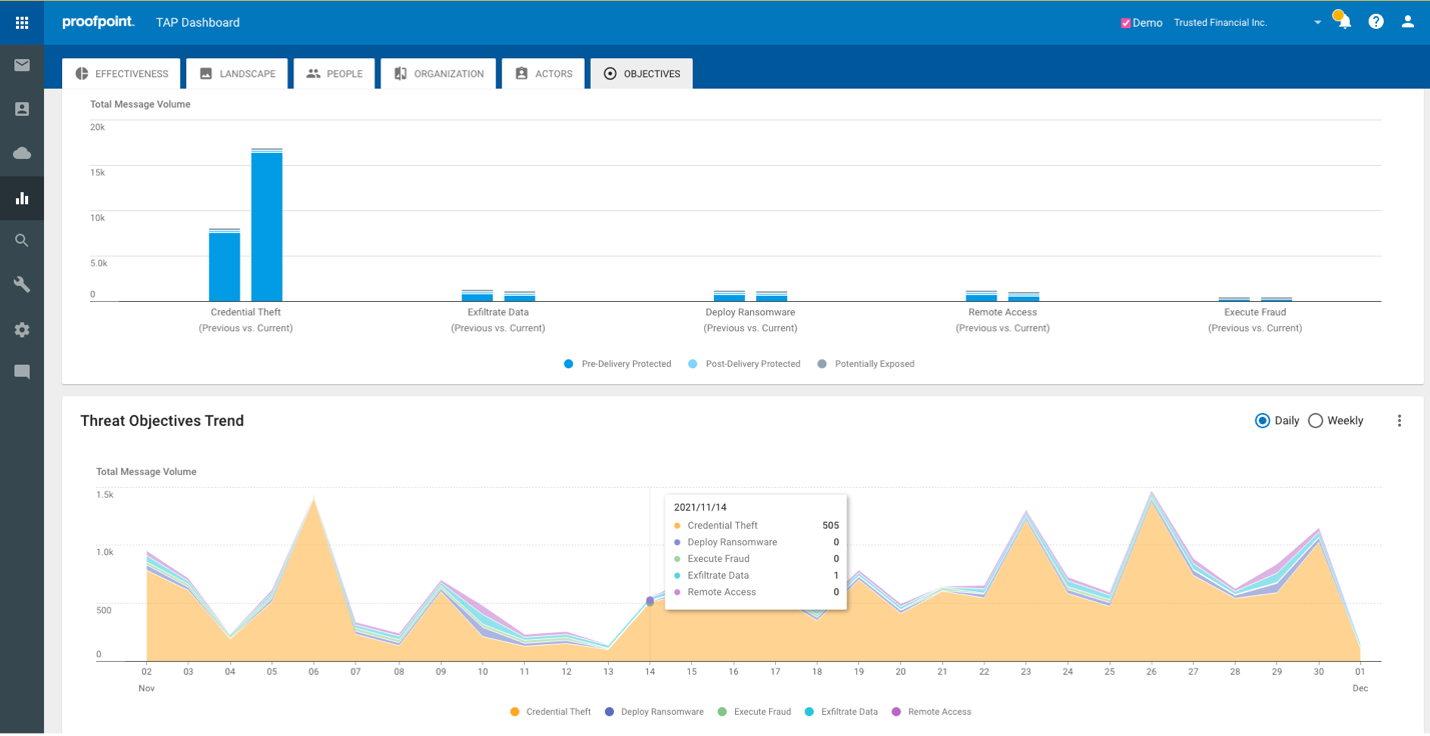
● Gain Actionable Visibility into Your Attack Surface: Proofpoint delivers actionable visibility to help you understand your attack surface – who your most attacked people are, what threats are targeting them, which suppliers pose risk – so you can prioritize risk mitigation controls like user training or isolation. This visibility into your very attacked people (VAPs) can also frame the security program in a new way that is understandable to executives and the board. And new features like threat objectives and user timelines provide context and new levels of people-centric visibility.
● Reduce Risk with an Integrated Threat Protection Platform: There’s no silver bullet in email security. Because there are multiple threats targeting your people, you need integrated, layered defenses to effectively protect against all the threats you’re concerned about – phishing, credential theft, ransomware, BEC, cloud account takeover, and compromised supplier accounts. Proofpoint provides an integrated threat protection platform that delivers synchronized, comprehensive controls across email, cloud, users and suppliers that enable you to more effectively reduce risk and downstream business impacts of email-based threats, such as ransomware.
● Improve Operational Effectiveness: More sophisticated threats and continuing cybersecurity talent/skills shortage lead to increased workloads for already strained security teams. Security analysts are dealing with alert fatigue and managing disparate, disjointed point products. Proofpoint increases the operational effectiveness of security teams by stopping more threats before they get into the organization, automating incident investigation and remediation, and delivering integrated workflows across products for a seamless experience. Customers have also adopted Proofpoint’s best-of-breed services to improve operations and alleviate the difficulty in hiring and retaining cybersecurity staff.



