Resecurity Context™ Cyber Threat Intelligence Platform
Photo Gallery
 |
 |
Resecurity Context™ Cyber Threat Intelligence Platform


Additional Info
| Company | Resecurity, Inc. |
| Website | http://www.resecurity.com |
| Company size (employees) | 50 to 99 |
| Type of solution | Cloud/SaaS |
Overview
Resecurity Context™ is a Cyber Threat Intelligence for production of finished intelligence including but not limited to IOCs, TTPs, threat artifacts.
To minimize the possibility of error, bias, and misinformation, Resecurity Context™ leverages data science and big data analytics to “mine” and analyze intelligence from a wide range of sources, including:
– Actor-Centric Intelligence
– Botnet Intelligence
– Dark Web Intelligence
– Data Breach Intelligence
– Human Intelligence
– Open-Source Intelligence
– Malware Intelligence
– ISP Traffic Intelligence
– Signal Intelligence
Platform ability to collect and analyze input from all these sources, Resecurity Context™ can provide comprehensive finished intelligence about subjects of interest (SOI) or multiple Essential Elements of Information (EEI), including but not limited to:
– Adversaries, Suspects, and Victims
– Device Identifiers
– Indicators of Attack (IOAs)
– Indicators of Compromise (IOCs)
– Malware Artifacts
– Network Indicators (IP, Domain)
– Particular Signatures or Events
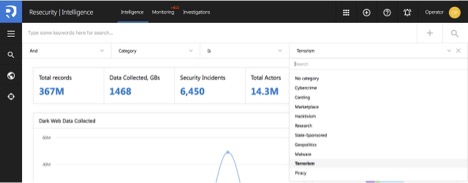
Resecurity Context™ has additional modules included in “Context Library” used for independent search, correlation and pivoting between different data sets and criteria, and monitoring operations.
Modules represent aggregated intelligence by the following categories:
– Intelligence (Dark Web, Deep Web, Surface Web) – by default;
– Data Breaches (Compromised Credentials, Data Leaks, Botnets, Third-party Data)
– Compromised Payment Data (Compromsied Credit Cards, Identity Information);
– Indicators of Compromise (IOCs Repository);
– IP Reputation
– Passive DNS (DNS
– Security Incidents
– Threat Actors (library of threat actor profiles).
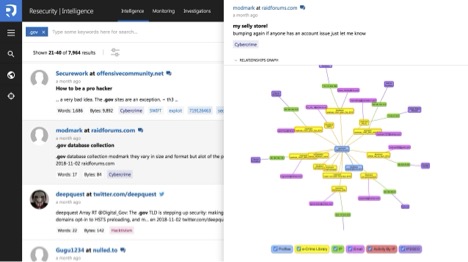
Resecurity Context™ allow operator to see what information is available to and being discussed by potential cyber-attackers.
In order to increase relevancy of the search results the operator may define exact category which will allow to prioritize the selection of sources, threat actors and other artifacts by thematic cluster (“niche”):
– Cybercrime (underground communities)
– Carding
– Marketplace (underground shops, illegal communities providing products or services)
– Hacktivism
– Research
– State-sponsored
– Geopolitics, Malware, Terrorism, and Piracy
AI-powered with robust ML framework used to generate actionable insights about potential cyber threats targeting your enterprise ecosystem.
SaaS-based intelligence-driven solution leveraging massive volumes of Big Data (13 billion threat artifacts) consumed from ongoing indexing of 35,435+ data points (Dark Web, Social Media Networks, Telegram, weChat, Viber, TOR, Jabber, IRC, etc.)
Native integration with SIEM/SOC/TIP and third-party cybersecurity solutions and systems, REST API.
How we are different
Key Differentiators:
1. All Source Intelligence
2. Not about open source but through human analyst
3. Commodity vs. Tailored Acquisition of intelligence specific to client needs.



