Silent Push Proactive Threat Intelligence Platform
Photo Gallery
 |

 |
Silent Push Proactive Threat Intelligence Platform

Additional Info
| Company | Silent Push |
| Website | https://silentpush.com |
| Company size (employees) | 10 to 49 |
| Headquarters Region | North America |
| Type of solution | Cloud/SaaS |
Overview
Silent Push reveals adversary infrastructure, campaigns, and security vulnerabilities by searching across the most timely, accurate and complete proactive threat intelligence dataset available anywhere in the world.
Defenders can focus on stopping threats before they cause a problem and significantly improving their security operations across the entire attack chain whilst simultaneously reducing operational complexity.
The Silent Push console and API exposes Indicators of Future Attack (IoFA) by applying unique behavioral fingerprints to attacker activity and searching across our dataset. Security teams can identify impending attacks, rather than relying upon out-of-date IoCs delivered by legacy threat intelligence platforms.
Our solutions include:
Proactive Threat Hunting – Identify and track malicious infrastructure before it’s weaponized.
Digital Risk Protection – Protect your brand from phishing, malvertisement, and spoofing attacks.
Early Detection Feeds – Monitor global threat activity with automated adversary intelligence.
Key Capabilities / Features
Indicators of Future Attack (IoFA) - Eliminates the need to rely on stale IOCs that solely relates to a single point in time. Enhances defense capabilities by enabling teams to focus on tracking and monitoring an adversary's underlying infrastructure and blocking before an attack.
Passive DNS lookups - Complete and categorical overview of the global IPv4 space, including domains and IP addresses, across the full catalogue of DNS record types.
One-click pivoting - Traverse attacker infrastructure without the need to perform complex lookups.
Data enrichment - Allows defenders to produce intelligence and hunt for threats by correlating the relationship between disparate malicious data types that wouldn’t ordinarily be associated with one another.
Silent Push API - Exposes individual endpoints across all backend systems, facilitating a variety of customer use cases and platform integrations
Integrated console (Silent Push GUI/Console) - Corroborates data sources and assigns risk/reputation scores to individual pieces of observable DNS data, including domains, IPs and nameservers. Allows for objective, evidence-based judgement calls that pinpoint observable data type as being engaged in malicious activity.
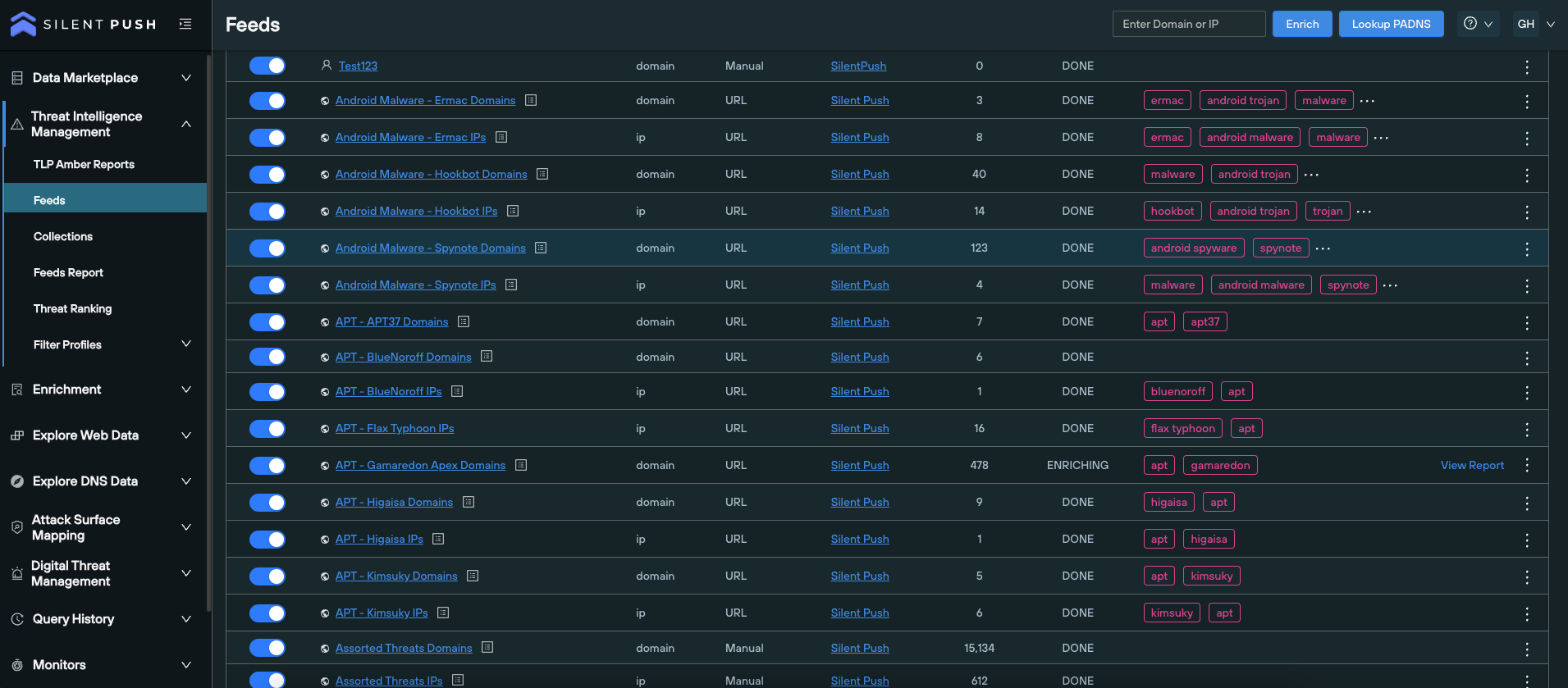
Monitoring - Monitor datasets for changes in the results, with email notifications sent every 24 hours.
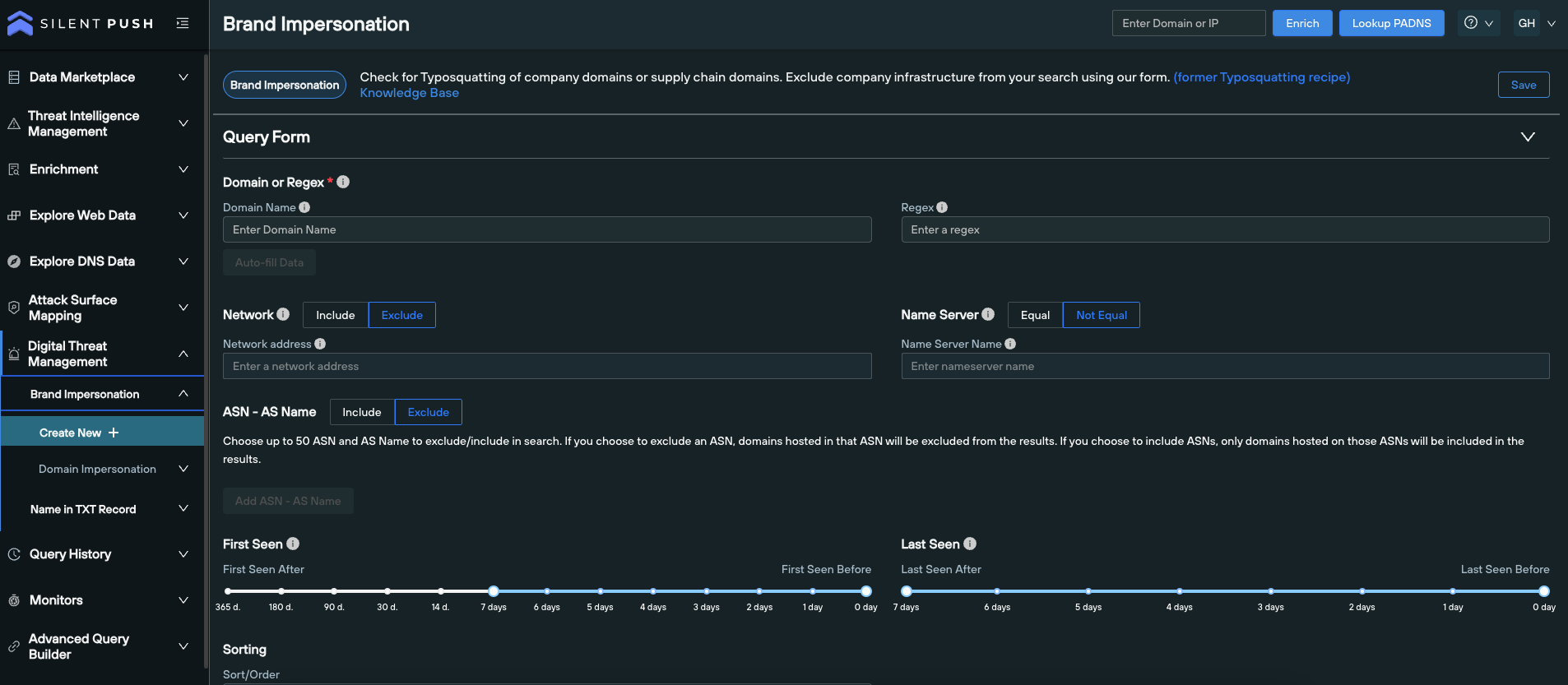
Brand impersonation - Locate spoofing domains masquerading as a legitimate brand name or supply chain operation. Minimizes the risk of financial and reputational harm that’s caused as a result for targeted brand spoofing.
Enhanced enumeration - Establish the presence of all observable data (subdomains, DNS record types etc,) across the global IPv4 space. Facilitates the timely, accurate and categorical mapping of an organization’s global DNS presence to identify exploitable assets and records.
How we are different
- Timely, accurate and complete first-party data is our core differentiator and sets Silent Push apart from legacy threat intel providers who don't own their own data.
- Our dataset is purpose built to understand the relationships between different pieces of infrastructure - we enjoy data independence and all that comes with it - agility, increased trust, accuracy, and speed.
- Legacy threat Intel providers cobble together data from numerous disparate sources. Legacy IOCs only provide generic, reactive information on known threats at a given point in time, and don’t provide security teams with an early warning of attacks or developing threats.



