STEALTHbits Privileged Activity Manager
Photo Gallery
 |

 |
STEALTHbits Privileged Activity Manager


Additional Info
| Company | STEALTHbits Technologies |
| Website | https://www.stealthbits.com/ |
| Company size (employees) | 100 to 499 |
| Type of solution | Software |
Overview
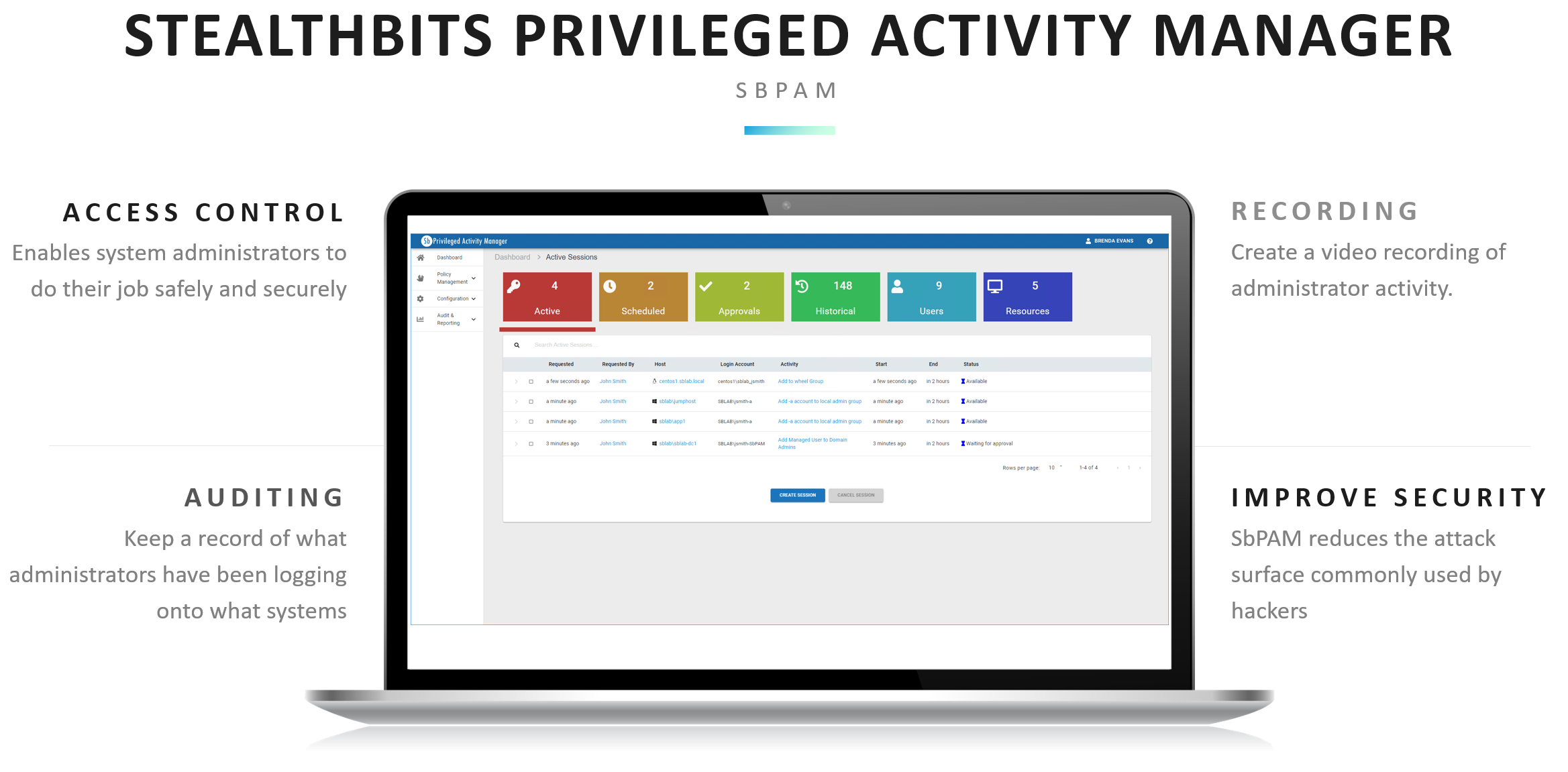
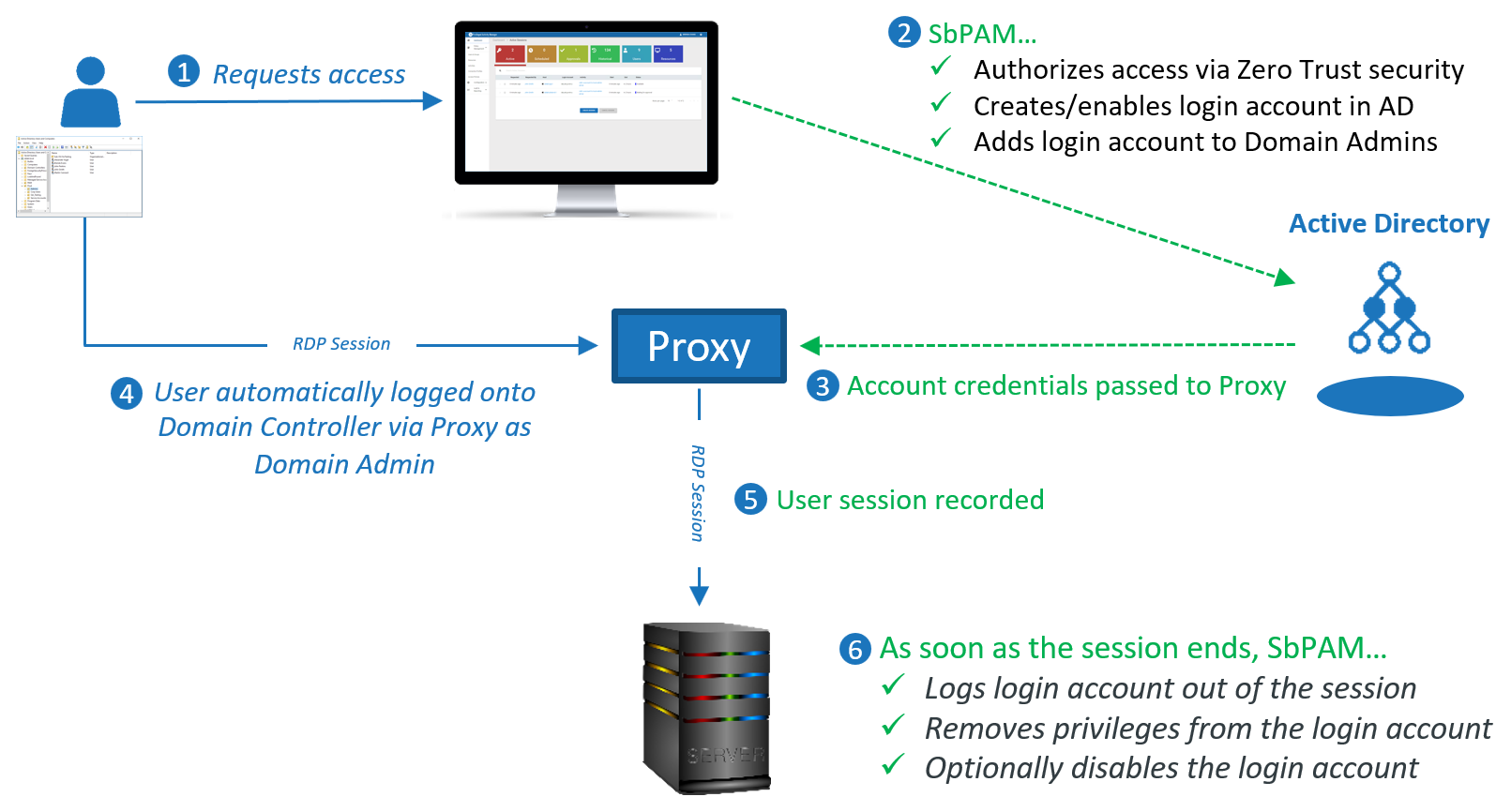
STEALTHbits Privileged Activity Manager (SbPAM) is a just-in-time task-based privileged access solution that reduces the privileged account attack surface left behind by traditional solutions.
Most Privileged Access Management (PAM) vendors focus on controlling access to privileged accounts such as Domain Admin, Administrator, and root. While this approach provides just-in-time access, the accounts still retain their privileges while not in use (known as standing privileges). The result is a widespread attack surface that can easily be compromised using modern cyber-attack techniques. This situation is compounded as organizations assign more managed accounts to each administrator.
SbPAM’s next generation zero standing privileges (ZSP) approach enables organizations to finally reduce their threat surface/standing privileges by eliminating commonly used privileged accounts and removing administrative privileges when not in active use.
SbPAM aims to provide a just-in-time task-based approach that provides an administrator/user with the exact level of privileges needed, exactly when they’re needed, for only as long as they’re needed, and returns the environment to a no-access-by-default state immediately upon completion.
How we are different
• Activity Based, No Standing Privileges – Unlike traditional PAM providers SbPAM focuses on the activities the administrator needs to perform, not on controlling access to accounts and their passwords. Traditional PAM results in an overabundance of privileged accounts and privileged access control groups with standing privileges to the resources they’re meant to secure. SbPAM provides Administrators the exact level of privileges needed, exactly when they’re needed, for only as long as they’re needed, and returns the environment to a no-access-by-default state, immediately upon completion.
• Bring Your Own Vault (BYOV) – Most traditional PAM vendors require the use of their password vault, often raising complexity and certainly raising costs. SbPAM contains a built in vault for credential management, but can uniquely map to vaults from other vendors in order to capitalize on exiting investments of time and money. Use an existing vault, our vault, or we can even provide a vault-less option…choice is yours.
• Delegate Administration & Record Sessions – Delegate administrative tasks to less-technical personnel safely to alleviate administrative burden. Develop Connection Profiles with policies to govern activities. Profile changes are made centrally and apply everywhere automatically. You can also enforce accountability or gain evidence during investigations with the ability to record and playback sessions. Know exactly what actions are taken with proof.



