Strobes Security
Photo Gallery
 |

 |
Strobes Security

Additional Info
| Company | Strobes RBVM (Risk-Based Vulnerability Management) |
| Website | https://strobes.co/ |
| Company size (employees) | 50 to 99 |
| Headquarters Region | North America |
| Type of solution | Software |
Overview
Strobes RBVM(Risk-Based Vulnerability Management) is your all-in-one platform, transforming complex vulnerability management into a streamlined operation. Identify, prioritize, and mitigate risks across all attack vectors, giving you complete control over your cybersecurity posture.
Key Capabilities / Features
Key Capabilities / Features
Vulnerability Aggregation-
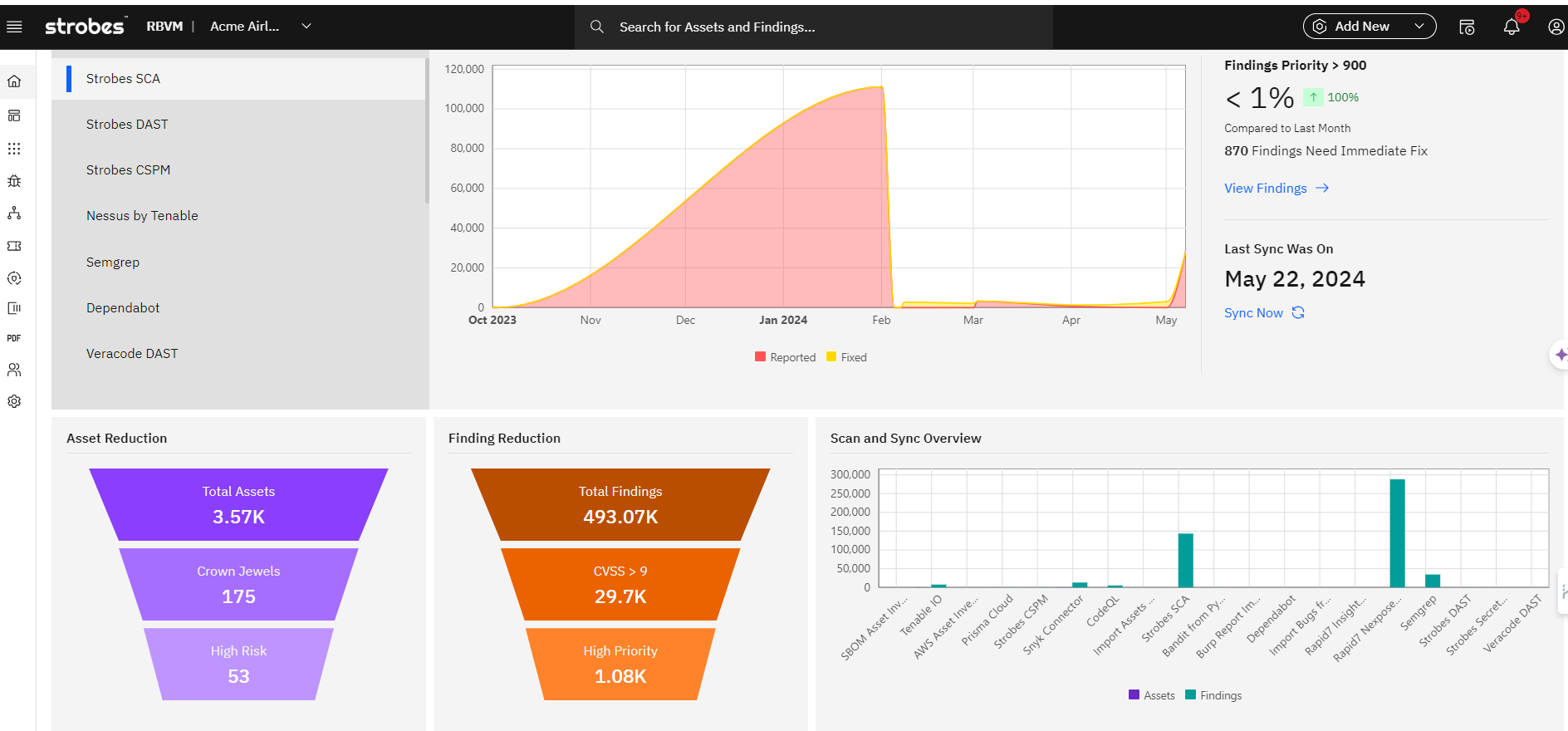
Unify your security data from various sources with our 100+ connectors, providing a comprehensive view of your threat landscape.
Remediation Orchestration-
Take action swiftly with automated workflows that guide you through the remediation process, minimizing exposure time.
De-duplication-
Analyze all of the ingested data into Strobes to analyze and deduplicate the vulnerabilities, thus reducing the number by manifolds.
Workflow Automation-
Automate tasks from quarterly scans to JIRA ticket creation and CI/CD pipeline-triggered remote scans, all seamlessly managed within Strobes.
Risk-prioritization-
Identify and tackle critical vulnerabilities first through intelligent threat intelligence, ensuring efficient resource allocation
How we are different
Strobes RBVM stands out from the crowd with three key differentiators:
1. 120+ Connectors: Unify Your Security Ecosystem
RBVM boasts an unmatched range of connectors (over 120!), seamlessly integrating with your existing security tools. Vulnerability scanners (SAST, DAST, Network), internal security teams, external vendors, bug bounty programs – you name it, RBVM connects to it. This eliminates data silos and redundant work, providing a single pane of glass view for all your vulnerabilities.
2. Scalability: Grows with Your Needs
RBVM is built to scale. Whether you’re a small startup or a sprawling enterprise, RBVM adapts to your evolving security landscape. As your attack surface grows, RBVM effortlessly scales to manage the influx of vulnerability data. This ensures you maintain comprehensive oversight without performance bottlenecks.
3. Data Consolidation: Actionable Insights at Your Fingertips
RBVM consolidates vulnerability data from across your entire security stack. Gone are the days of piecing together information from disparate sources. RBVM presents vulnerabilities in a unified format, allowing for efficient prioritization and remediation. This empowers your security team to focus on the threats that matter most, streamlining your vulnerability management process.



