ThreatAware
Photo Gallery
 |
ThreatAware
Additional Info
| Company | ThreatAware |
| Website | threataware.com |
| Company size (employees) | 10 to 49 |
| Headquarters Region | Europe |
| Type of solution | Cloud/SaaS |
Overview
ThreatAware is a groundbreaking Cyber Asset Management platform that’s revolutionising asset and security tool management for organisations worldwide. With years of experience in looking after complex IT environments, we saw an increase in cyber-attacks, despite the number of security tools being bought.
Robust cyber hygiene is considered the most effective defence against attacks, but our data shows that c.30% of active devices lack fundamental security controls. Since 2018, we’ve been on a mission to empower organisations in their defence against cyber threats, emphasising the importance of discovering and protecting every asset to gain a single source of truth.
We believe that:
Unified data empowers holistic visibility.
Robust cyber hygiene is the most effective defence.
Simplicity drives action.
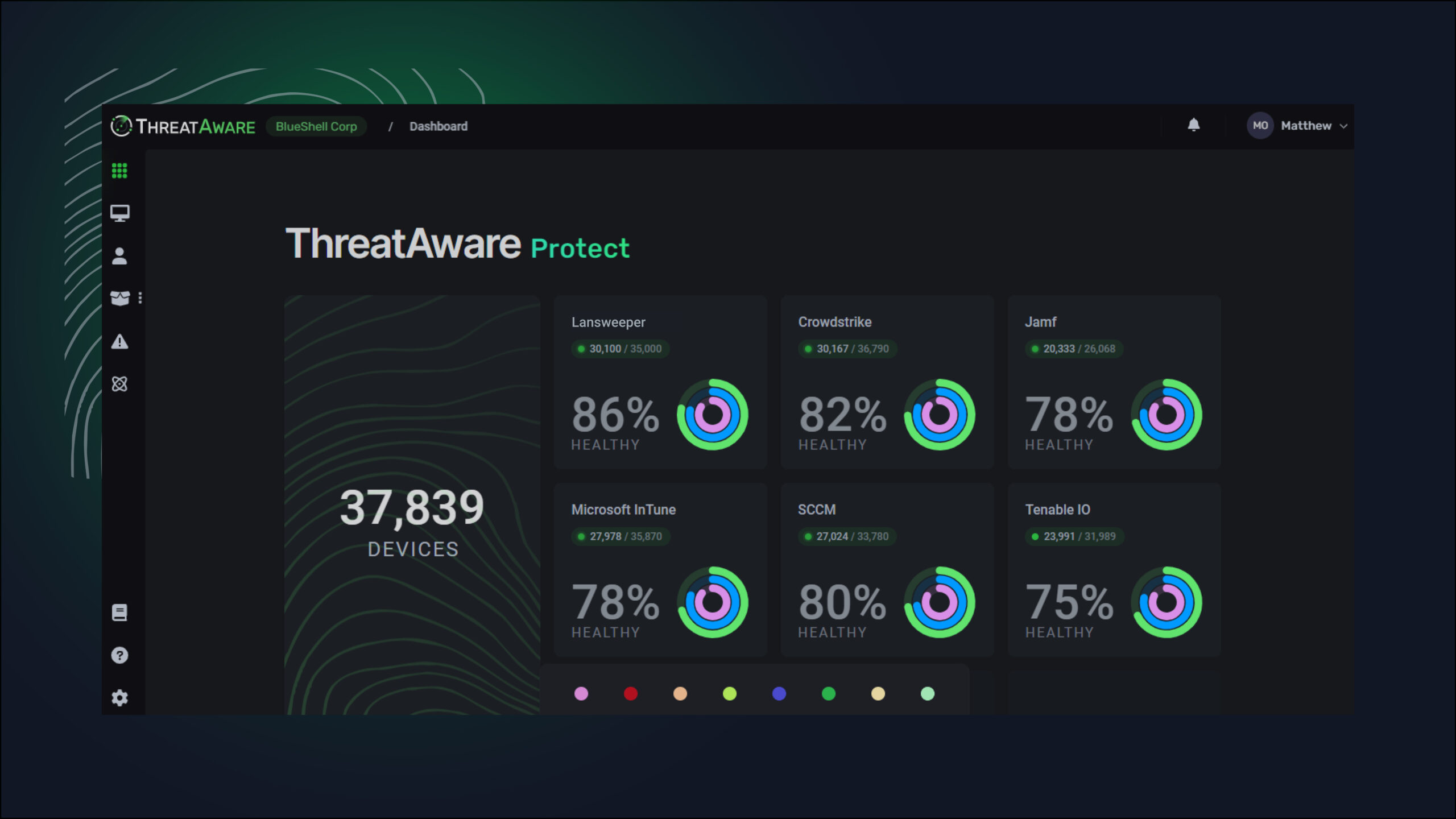
ThreatAware provides companies of all sizes, across a range of sectors, with a platform that continuously monitors their IT landscape from one screen. Through our unparalleled patent-pending timeline-matching technology, ThreatAware gives customers:
Stronger attack surface management: Traditional methods of managing attack surfaces often fall short, leaving potential vulnerabilities. We give organisations real-time visibility into their entire IT estate, highlighting vulnerabilities.
Continuous security controls monitoring: ThreatAware provides continuous, automated critical controls monitoring to help organisations maintain compliance, reduce vulnerabilities and enhance security.
Efficient risk reporting: We offer accurate, comprehensive and accessible reports that support organisations to make informed decisions and investments in their approach to cyber risks.
Streamlined asset management: Through API discovery, time-matching and dynamic configuration, the ThreatAware platform consolidates and contextualises information into a single, accurate asset list.
Efficient vulnerability management: Our platform highlights devices lacking patching agents and seamlessly integrates with multiple products, giving organisations a clear list of assets and their vulnerabilities with minimal effort.
Effective lifecycle management: ThreatAware provides comprehensive lifecycle management, including a consolidated view of user accounts associated with various systems.
Key Capabilities / Features
At ThreatAware, we're dedicated to empowering our customers in their defence against cyber threats, emphasising the importance of discovering and protecting every cyber asset. Our platform plays a pivotal role in developing robust cyber resilience strategies.
Here's a snapshot of our key use cases:
1. Stronger Attack Surface Management: Traditional methods often fail to provide a comprehensive view of the entire IT estate, leaving potential vulnerabilities. ThreatAware addresses this by offering effective cyber asset management, providing visibility into the entire IT estate and highlighting areas vulnerable to attack.
2. Continuous Security Controls Monitoring: Achieving standards like Cyber Essentials and ISO 27001 requires efficient monitoring of critical controls. ThreatAware provides automated continuous controls monitoring, ensuring compliance and reducing vulnerabilities. Client's achieve significant improvements in deployment and configuration since using our platform.
3. More Efficient Cyber Risk Reporting: Producing accurate and understandable cyber risk reports is challenging, but ThreatAware simplifies this process with accessible and easy-to-understand reports. Leading global businesses rely on ThreatAware for auditing and Cyber Essentials accreditation.
4. Streamlined Asset Management: Managing assets across a fragmented IT landscape is difficult, but ThreatAware addresses this challenge through API discovery and dynamic configuration. Businesses and MSPs use ThreatAware to streamline asset management across multiple locations.
5. Efficient Vulnerability Management: Identifying assets with missing patching agents and addressing vulnerabilities can be complex, but ThreatAware simplifies this process with custom views and seamless integration with vulnerability scanners.
6. Effective Lifecycle Management: Cloud adoption and hybrid working have made lifecycle management challenging, but ThreatAware provides comprehensive user and device management. Our platform offers instant visibility into devices accessing corporate systems and highlights unused accounts for removal.
How we are different
What makes us different?
ThreatAware is revolutionising asset and security tool management for organisations across the globe. A key challenge in cyber asset management is being able to find all your assets in a modern, usually fragmented IT estate. Agent-based methods, such as CMDB or log ingestion methods such as SIEM, are unable to do this successfully. Instead, ThreatAware gathers data directly from security tools’ cloud consoles, consolidating that data into a contextualised single list to provide a highly accurate picture of the entire estate.
Through our unparalleled, patent-pending timeline-matching technology we provide an accurate, non-duplicated asset inventory and groundbreaking real-time insight into the deployment, functionality and health of all security tools. Our matching algorithm offers remarkable accuracy, swiftly and without hassle. It provides organisations with a single source of truth, with full confidence. Our approach is pioneering and unmatched in its accuracy, even when the data sources are incomplete. We can uncover 10-30% of unknown assets within an organisation’s enterprise, including those lacking crucial security tools – all without the need to install additional software or hardware.
A standout feature of the ThreatAware platform is this unique ability to seamlessly connect to security tools and cloud directories via API. This enables us to onboard a new organisation in under 30 minutes, with no need for the installation of an appliance or agents. ThreatAware can identify gaps in tool deployment and functionality straight out of the box, delivering immediate value for organisations without building or coding.
-
Vote for this Nomination
(click the thumbs-up icon to cast your vote)

 (1 votes)
(1 votes)You need to be a registered member to vote for this nomination. Please register here.


