ThreatDefence Cyber Range Platform
Photo Gallery
 |
 |
ThreatDefence Cyber Range Platform
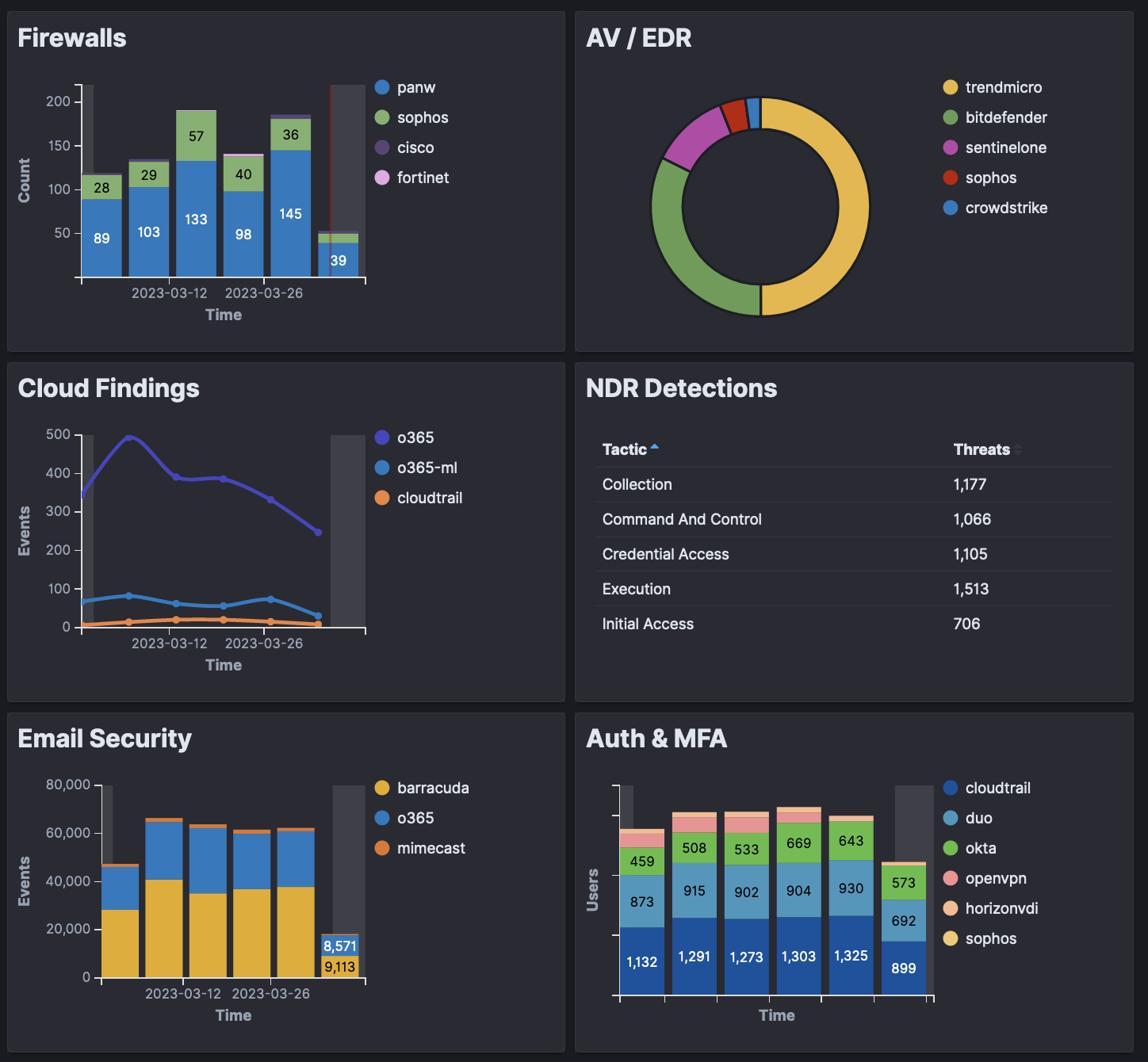
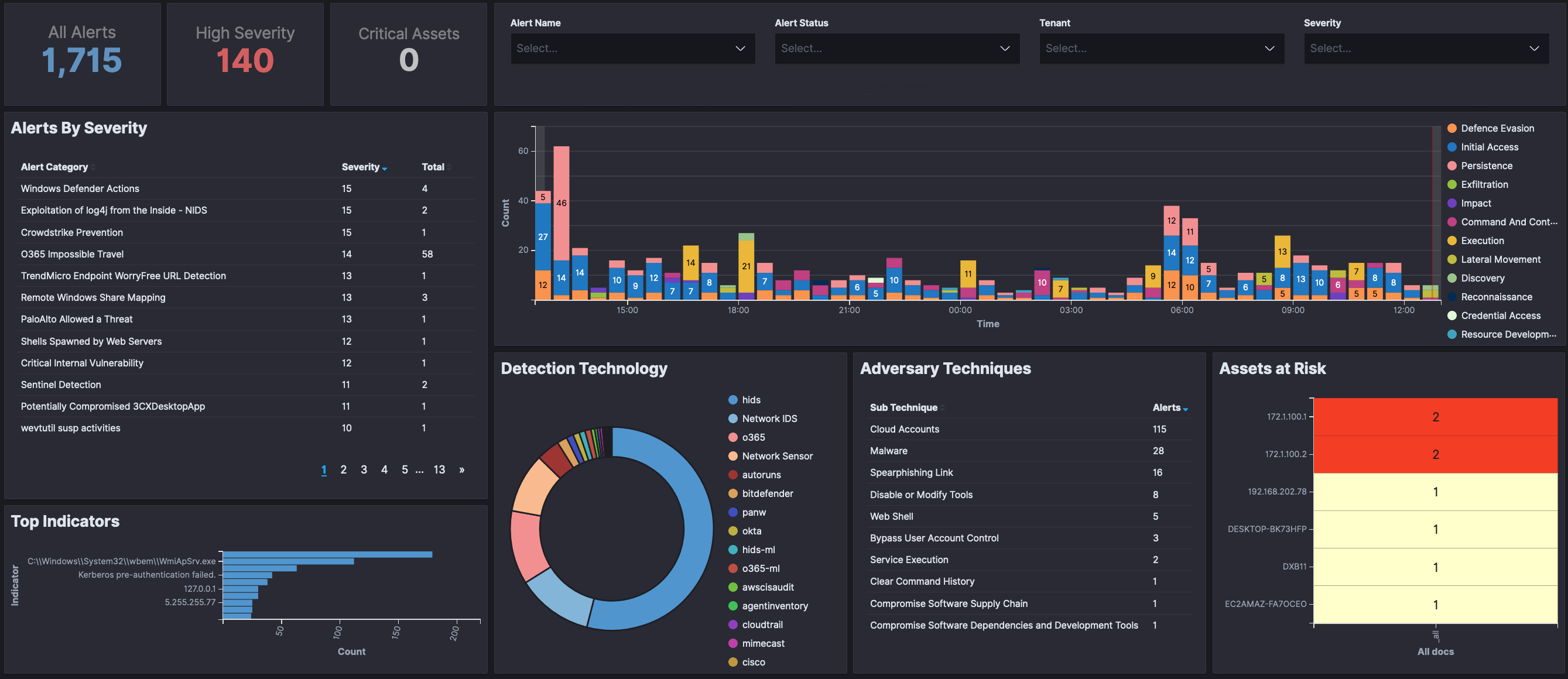
Additional Info
| Company | ThreatDefence |
| Website | https://www.threatdefence.com |
| Company size (employees) | 10 to 49 |
| Headquarters Region | Asia |
| Type of solution | Cloud/SaaS |
Overview
ThreatDefence offers a comprehensive cyber range and cyber attack simulation solution that enables organizations to develop their cyber skills using real data and real adversarial attacks recorded during actual cyber incidents. Our solution provides a hands-on, real-world training experience that empowers SecOps teams to respond quickly and effectively to real-life cyber threats.
At ThreatDefence, we prioritize the value of practical, real-world cyber security training that can be applied directly to the environment that trainees work in. We provide a virtual cyber range solution that allows organizations to create replicas of their real systems, cloud environments, and networks. This approach ensures that trainees are training on scenarios that are relevant to their job or desired career path and can be immediately applied to their day-to-day work.
Our training scenarios are intentionally designed to be complex and open-ended, and require critical thinking and creative problem-solving skills to address realistic cyber threats. The simulations are organized based on the MITRE ATT&CK framework, which provides a common language for discussing and understanding the various phases of a cyber attack. Our solution goes beyond just training on theoretical concepts; we emulate real adversaries like APT29, running their tools, techniques, and tactics on your cyber range. By modeling adversarial behavior and objectives, such as data exfiltration, espionage, or ransomware deployment, trainees are able to develop a comprehensive understanding of real-world threats and how to defend against them.
Key Capabilities / Features
Our cyber security simulations allow organizations to simulate any kind of attack scenario, including zero-day or supply chain attacks, when one of your critical suppliers or software modules is compromised. These simulations put trainees into real cyber crisis scenarios, adding group collaboration and time pressure, further enhancing the effectiveness of the training. The training scenarios can last multiple days, providing trainees with a thorough understanding of how to handle a complex cyber security incident from start to finish.
How we are different
- hyper-realistic cyber security simulations
- recorded real attacks and attack data
- simulation of zero-day and APT scenarios.
-
Vote for this Nomination
(click the thumbs-up icon to cast your vote)

 (0 votes)
(0 votes)You need to be a registered member to vote for this nomination. Please register here.


