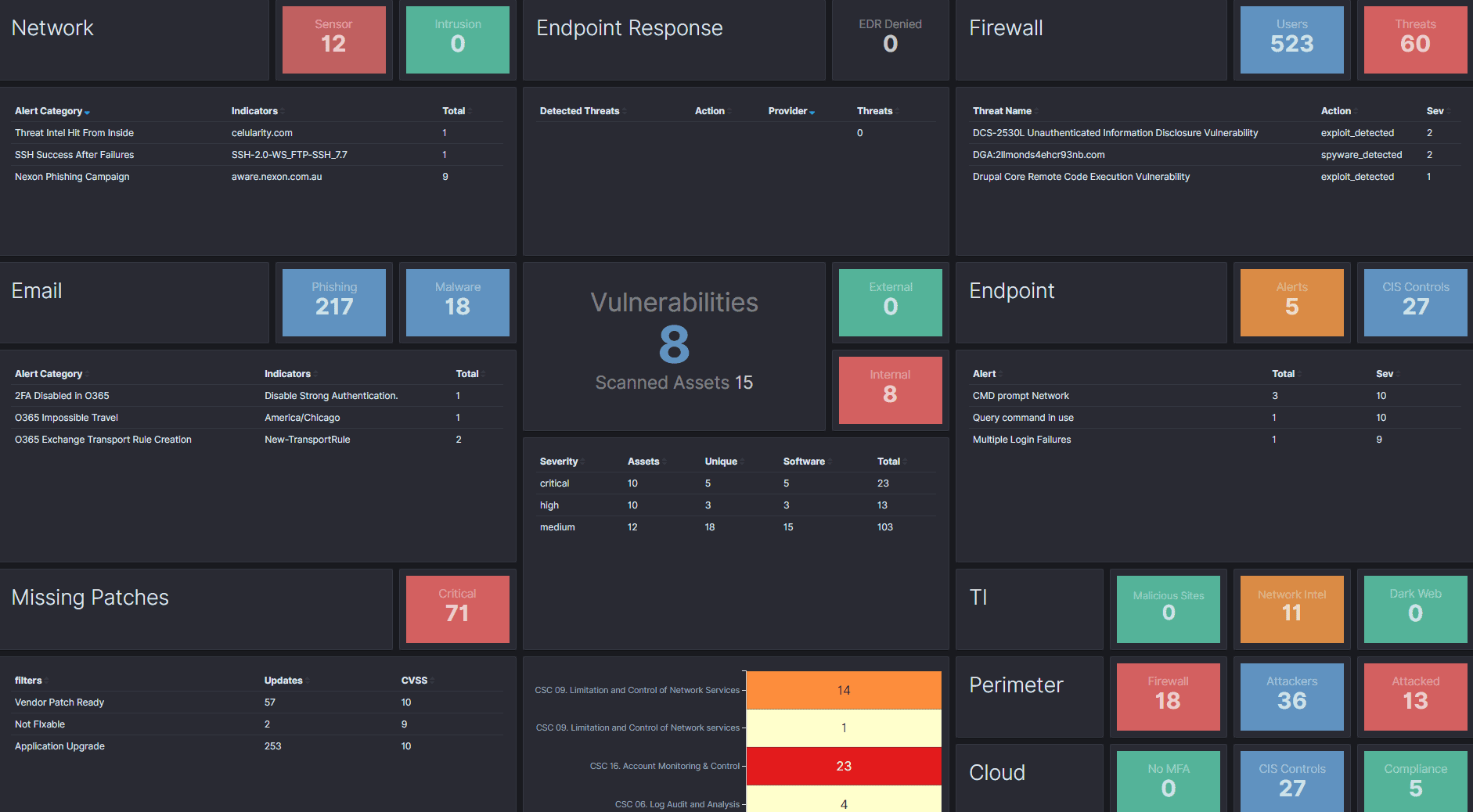
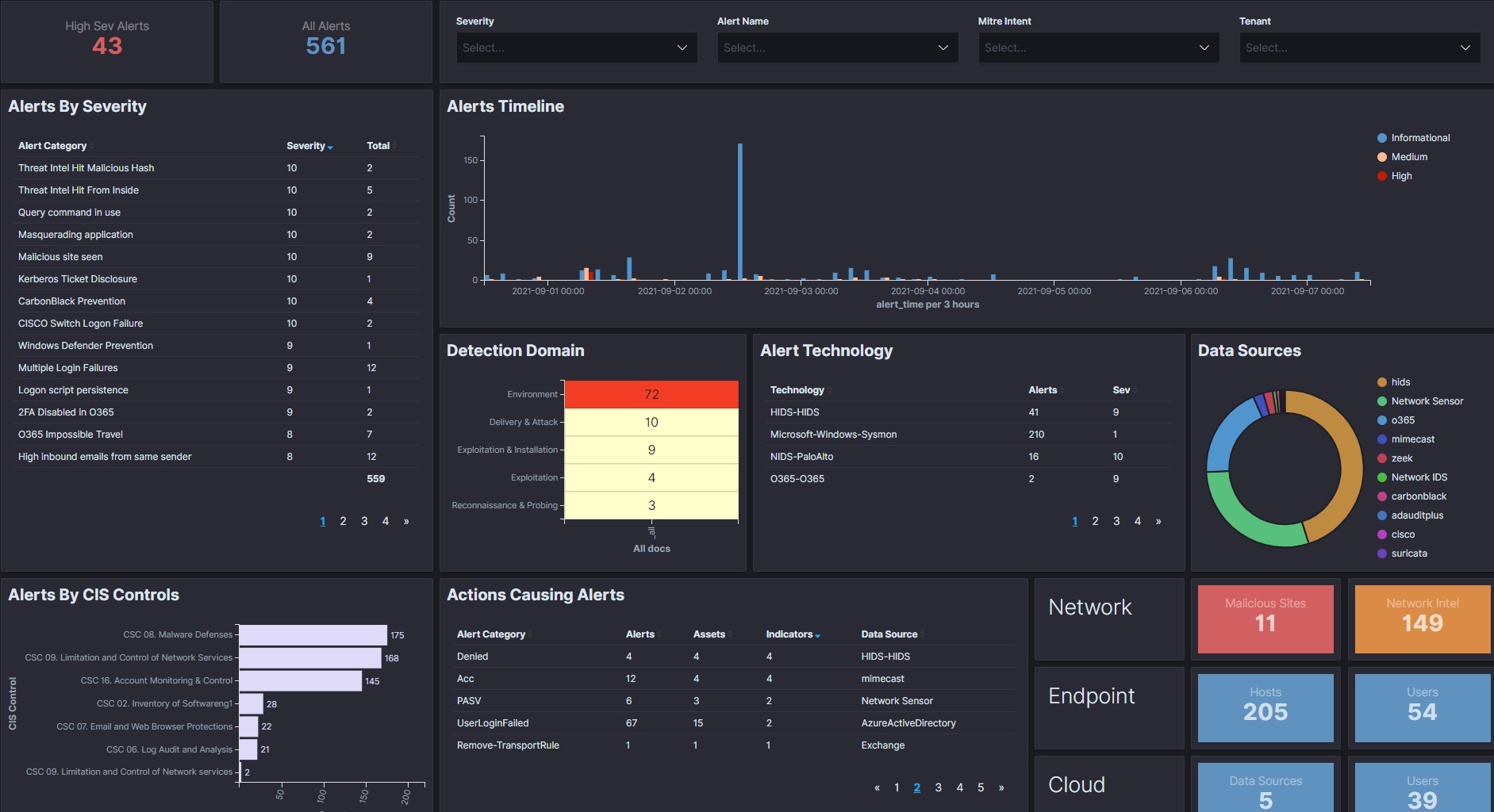
ThreatDefence XDR/MDR Platform
Photo Gallery
 |
 |
ThreatDefence XDR/MDR Platform

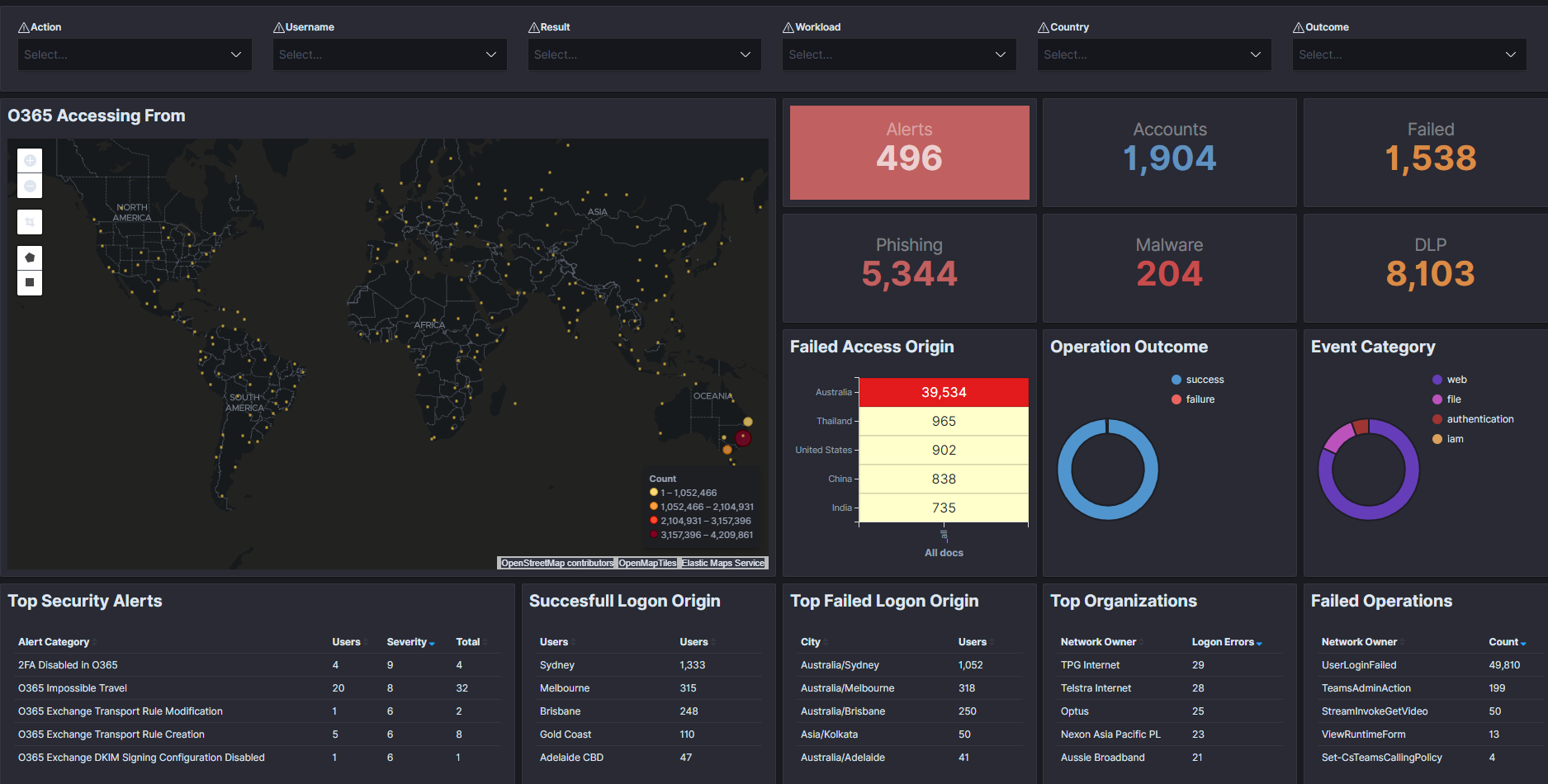
Additional Info
| Company | ThreatDefence |
| Website | https://www.threatdefence.com |
| Company size (employees) | 10 to 49 |
| Type of solution | Cloud/SaaS |
Overview
Our MDR provides great visibility into your environment and end-to-end coverage of your attack surfaces. You will get real-time threat detection, 24×7 threat hunting, thorough investigations and full incident response lifecycle support.
Our focus is not on raising alerts, but on delivering great security outcomes and defending your business from disruptions and data breaches.
Our XDR Platform employs deep data visibility, machine learning, advanced correlations and built-in automation, allowing security teams to focus on what really matters, filtering out noise and false positives, and produce high fidelity detections. The detections support our human-led investigations and real-time threat hunting to reveal the most hidden and unknown threats. Our 24×7 SOC as a Service is staffed with experienced security analysts with CISSP and OSCP certifications providing advanced threat analysis, tactical threat intelligence and incident response.
Sophisticated attackers can be moving across your network for months, stealing intellectual property, data, and user credentials, while staying undetected. Our proactive threat hunting identifies unknown threats not visible to standard security tools, helps to prevent attackers from evading your security defences.
Our expert threat hunters gain insights from your security data, deep diving into any anomalies, suspicious events, and any unexpected behaviors observed on your network. As part of our security operations, we not only find previously undetected threats, but also enhance your detection capability by adding new rules and fine tuning the platform to stay ahead of attackers.
How we are different
Our platform provides:
1. AI-assisted threat hunting, investigation, and incident response, providing automated threat detection, containment, and artefact acquisition.
2. Enterprise-wide digital forensics capability, enabling security analyst to run forensic searches remotely over unlimited number of endpoints
3. Deep real-time visibility across the entire attack surface, recording even the most subtle security events missed by our competitors.



