VMware NSX Network Detection and Response
Photo Gallery
 |

 |
VMware NSX Network Detection and Response


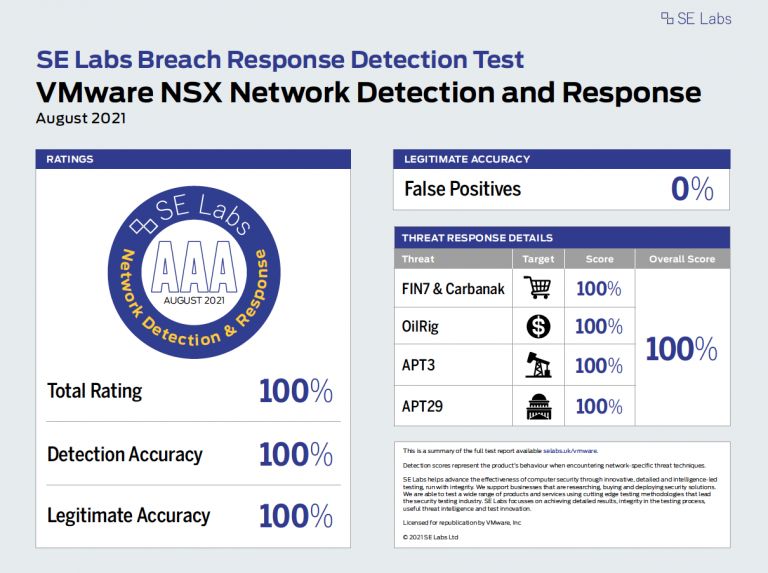
Additional Info
| Company | VMware |
| Website | http://www.vmware.com |
| Company size (employees) | 10,000 or more |
| Type of solution | Software |
Overview
VMware NSX NDR provides a tightly integrated set of network detection and response capabilities for east-west security within the data center and multi-cloud environments. The solution has the broadest set of detection capabilities that span network IDS/IPS, behavior-based network traffic analysis, and includes the VMware NSX Advanced Threat Analyzer™, a sandbox offering based on a full-system emulation technology that has visibility into every malware action. Powered by AI, NSX Network Detection and Response correlates individual detection events across multiple assets and hops into fewer security-relevant intrusions, organizing them into a timeline for rapid threat hunting and response. Together, the detection capabilities provide the most effective prevention of lateral movement and comprehensive protection against a wide range of known and unknown advanced threats.
How we are different
Most accurate threat detection: Network traffic analysis (NTA) applies unsupervised machine learning (ML) to network traffic to detect protocol and traffic anomalies and uses supervised ML to automatically create classifiers that recognize malicious network behaviors and previously unknown malware. The solution applies AI to the malicious behaviors and malware samples collected from customers and partners across a global threat intelligence network to automatically create new IDS/IPS signatures and push them out to all NSX sensors at scale. The patented NSX Advanced Threat Analyzer deconstructs every behavior engineered into a file or URL to determine if it is malicious. It sees all instructions a program executes, all memory content and all operating system activity. The VMware Threat Analysis Unit continuously updates VMware NSX NDR in real time with threat intelligence, such as active command and control (C&C) servers, objects with zero-day exploits, toxic websites and malware distribution points, and malware information useful to defend against threats specific to organizations.
Highest fidelity alerts: SOC teams are overwhelmed by the high volume of low-fidelity alerts generated by security controls. The unique combination of AI-powered NTA, IDS/IPS and threat analysis slashes false positives by up to 90 percent and provides unmatched visibility. Massive amounts of network data down are condensed down to just a handful of intrusions, meaning analysts can spend time solving real incidents and rather than chasing false positives.
Visualize the entire attack chain: Aligned with the MITRE ATT&CK framework, VMware NSX NDR classifies malicious activity by attack stage to identify the risk associated with each event. It also generates a dynamic intrusion blueprint and a detailed timeline of a threat as it enters and moves laterally across your on-premises and cloud network. These visualizations give SOC team the information needed to quickly understand the scope of attacks and prioritize responses.



