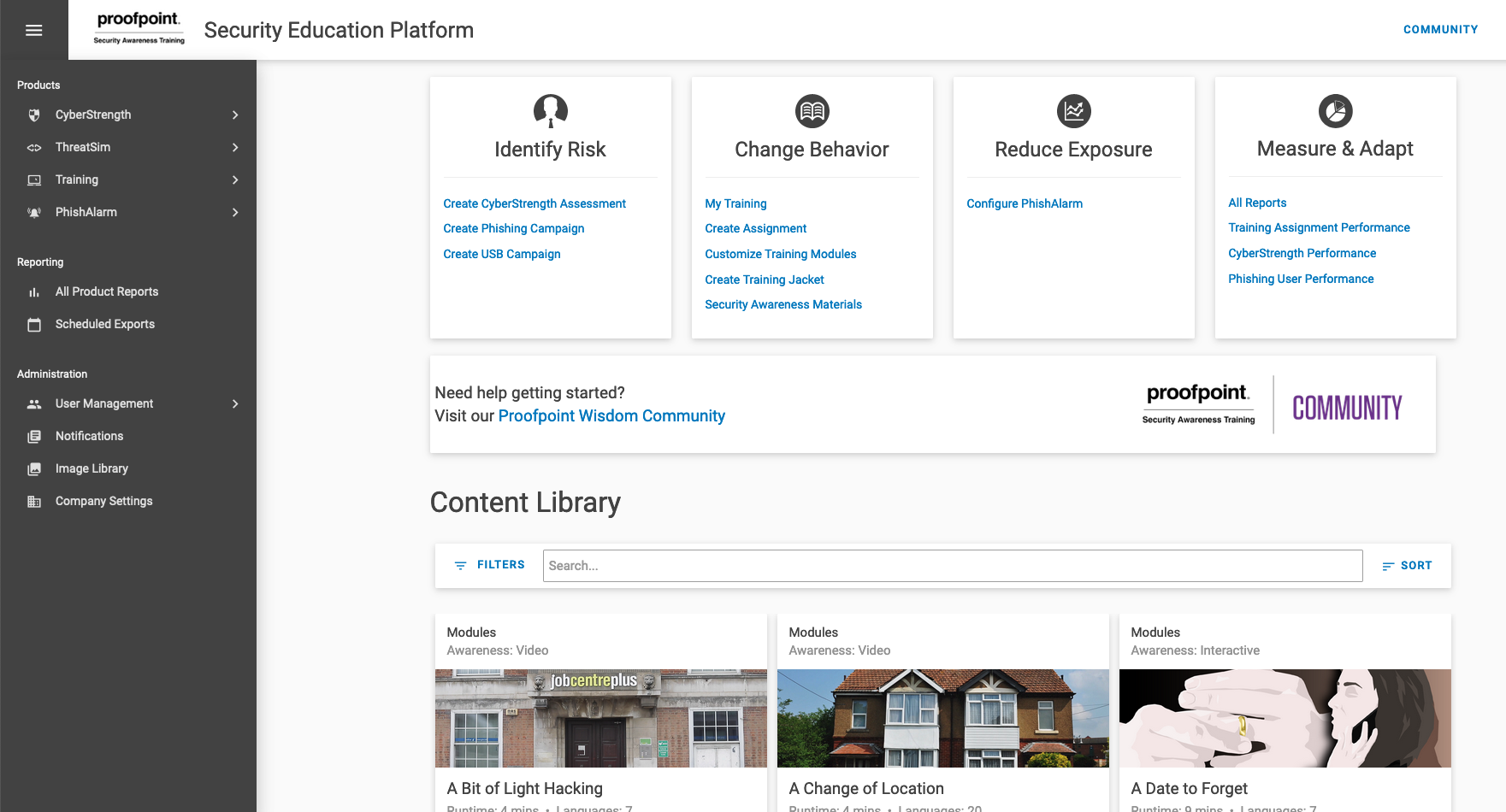
Proofpoint Security Awareness Training
Photo Gallery
 |

 |
Proofpoint Security Awareness Training

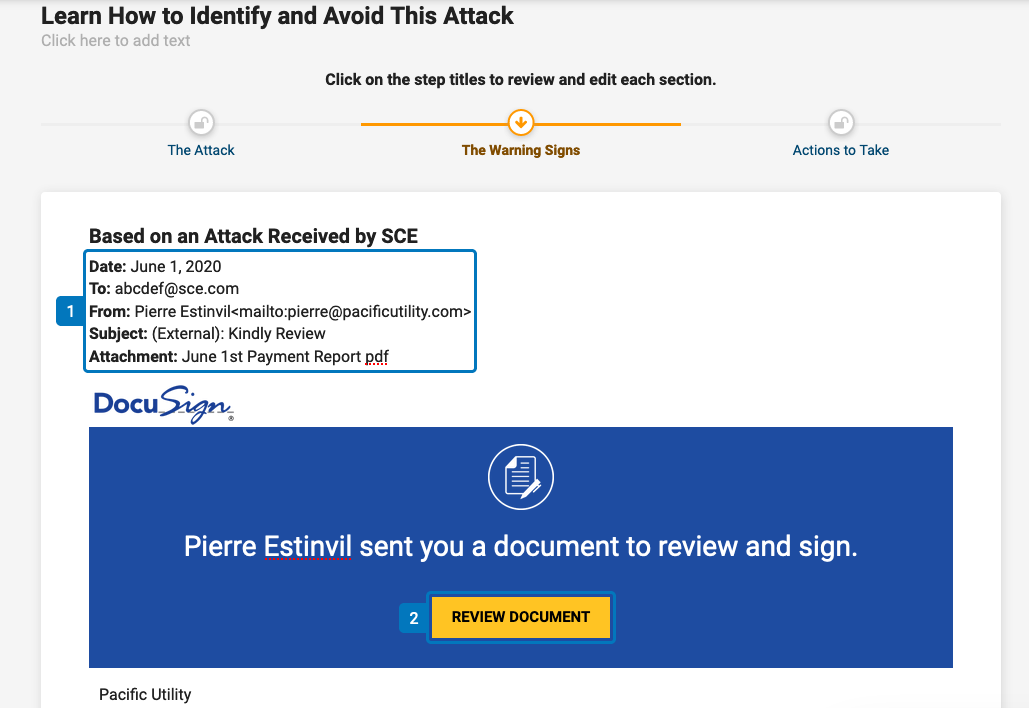

Additional Info
| Website | https://www.proofpoint.com/us |
| Company size (employees) | 1,000 to 4,999 |
| Headquarters Region | North America |
Overview
Leading organizations of all sizes, including more than half of the Fortune 1000, rely on Proofpoint’s people-centric security and compliance solutions to mitigate their most critical risks across email, the cloud, social media, and the web. There are thousands of enterprise Proofpoint Security Awareness Training customers who have trained over 33 million users in the past year.
How we are different
• Proofpoint is making it easier for customers to maximize their limited security awareness time budget and make a real impact. We do this by providing industry-first insights to focus their education, including: Users engaging with real malicious messages, top users being targeted by attackers, and detailed information about the types of messages users are reporting (safe, malicious, etc.). These insights means administrators can provide more relevant and impactful education to users who need it most based off of real-world data.
• We consistently hear from customers who have utilized multiple security awareness training vendors, or even left us before and come back, that users prefer and get the most value out of our education. We follow a proven methodology of providing short, impactful education using proven learning science to maximize retention. With full customization capabilities available to administrators, users get a tailored educational experience using verbiage and imagery that resonates with them. And they get the education when they need it, so lessons are relevant to their real experiences and risk levels.
• Our email reporting, analysis, and remediation solution automates the entire incident response process and reduces IT and security overhead for already busy teams. Users can with one click easily report messages on any device with our new HTML-based email warning tags that provide nudges if a message might be risky right in the email. Users then get customized feedback based on if their message is safe, malicious, or otherwise, providing them guidance to hone their phish-spotting skills.



