ThreatQ Investigations
Photo Gallery
 |
 |
ThreatQ Investigations


Additional Info
| Company | ThreatQuotient |
| Website | https://www.threatq.com/ |
| Company size (employees) | 100 to 499 |
| Type of solution | Software |
Overview
ThreatQuotient believes that threat data and intelligence are the most valuable tools to detect, prevent and respond to threats. It provides the context and foundational understanding that is needed for effective security operations. To make use of this, however, organizations need an approach to security operations that relies on a single, systemic security architecture that supports all teams and use cases while continuously improving.
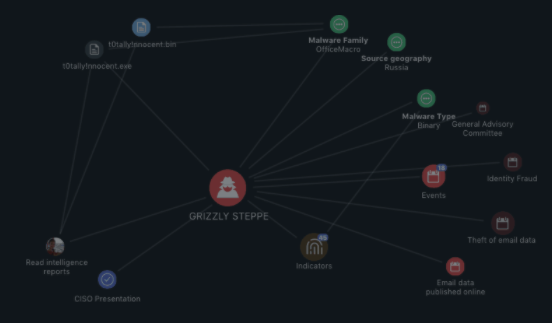
ThreatQuotient offers ThreatQ Investigations, the industry’s first cybersecurity situation room designed for collaborative threat analysis, shared and accelerated understanding, and coordinated response. Built on top of the ThreatQ Platform, ThreatQ Investigations allows for the capturing, learning and sharing of knowledge.
Use cases for ThreatQ Investigations include: anticipation situations that accelerate understanding of emerging threats to update defense posture proactively; response situations that enable the right responses to be determined and acted upon faster than previously possible; and retrospective analysis to learn what can be improved.
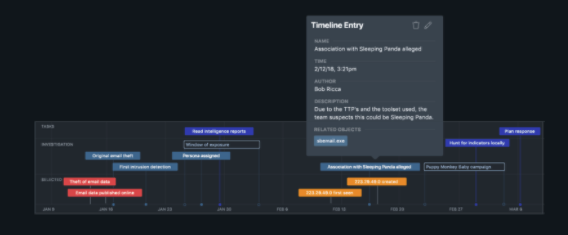
The ThreatQ Platform and ThreatQ Investigations are designed to support the fact that incident response is a team sport. Starting with importing an event/investigation, incident responders can immediately assess what other research has been performed and by whom, what tasks need to be assigned, and how all the data relates. As responders from around the organization complete tasks and publish them to the larger incident canvas, the team progresses towards identifying patient-0 and re-arming the organization against the next wave of attacks.
If a team knows their attackers’ tactics, techniques and procedures (TTPs), then as that intelligence comes in, they can be scored appropriately and even be added to a “watchlist” for visibility. This is a subtle and proactive way to keep a finger on the pulse of malicious activity. When adversary profiles are frequently updated and maintained with the latest attributes, new analysts can learn about the adversary exponentially faster.
How we are different
ThreatQ Investigations accelerates understanding: Users can instantaneously transfer knowledge, reduce mean time to detect (MTTD) and mean time to respond (MTTR). By maintaining adversary profiles and associated malware analysis in ThreatQ, an IR team using ThreatQ Investigations instantly knows the TTPs of that adversary. Having an adversary dossier via the Kill Chain is an extremely powerful “tactical operations guidebook” allowing even junior analysts to work far beyond their experience.
The greatest impact of ThreatQuotient’s solutions comes from breaking down silos and enabling teams to share intelligence and tasks easily, supporting the many teams within an organization responsible for security – Security Operations Center (SOC), Incident Response (IR), Risk Management, Vulnerability Management, Endpoint and Network teams, etc.
ThreatQuotient believes a threat-centric approach to Security Operations improves overall efficiency, consistency and effectiveness and empowers security professionals with more control.



